Email continues to be the primary attack vector for cybercriminals targeting organizations across all industries. These attacks arrive disguised as legitimate communications, often mimicking trusted senders and creating a false sense of security that bypasses technical defenses by taking advantage of human error. Understanding the distinctions between business email compromise (BEC) vs phishing is crucial, as both represent sophisticated yet very different threat methods.In this article, we’ll go over what a BEC attack looks like, what makes a BEC attack different from a typical phishing email attack, recent trends, and what you can do to prevent these types of attacks.
Key Takeaways for Business Email Compromise vs Phishing
- BEC attacks and phishing attacks are similar in that they both use social engineering tactics, typically involve email as an attack vector, and the end goal is often financial gain, data theft, or unauthorized access.
- While BEC attacks and phishing are similar, BEC issues are far more sophisticated and personalized to the target.
- Best practices for preventing BEC attacks include training employees, using MFA, and implementing DMARC protocols.
Is Business Email Compromise the Same as Phishing?
When asking how to deal with business email compromise vs phishing attacks, the truth is that most email security solutions can handle both in similar ways. BEC and phishing attacks are closely related and often overlap, as both rely on deception to trick victims into taking harmful actions. However, they differ in execution, targeting, and sophistication.
Similarities Between BEC and Phishing
- Both use social engineering tactics to manipulate victims.
- Both typically involve email as the primary attack vector.
- The end goal of both is often financial gain, data theft, or unauthorized access.
Differences Between BEC and Phishing
- Targeting: BEC attacks are highly targeted, often aimed at specific individuals like executives or finance personnel, while phishing is usually broader and sent to large groups.
- Tactics: BEC relies on impersonation and pretexting without malware or links, whereas phishing often uses malicious links or attachments to compromise systems.
- Complexity: BEC attacks are generally more sophisticated and customized, requiring research and planning, whereas phishing is typically automated and generic.
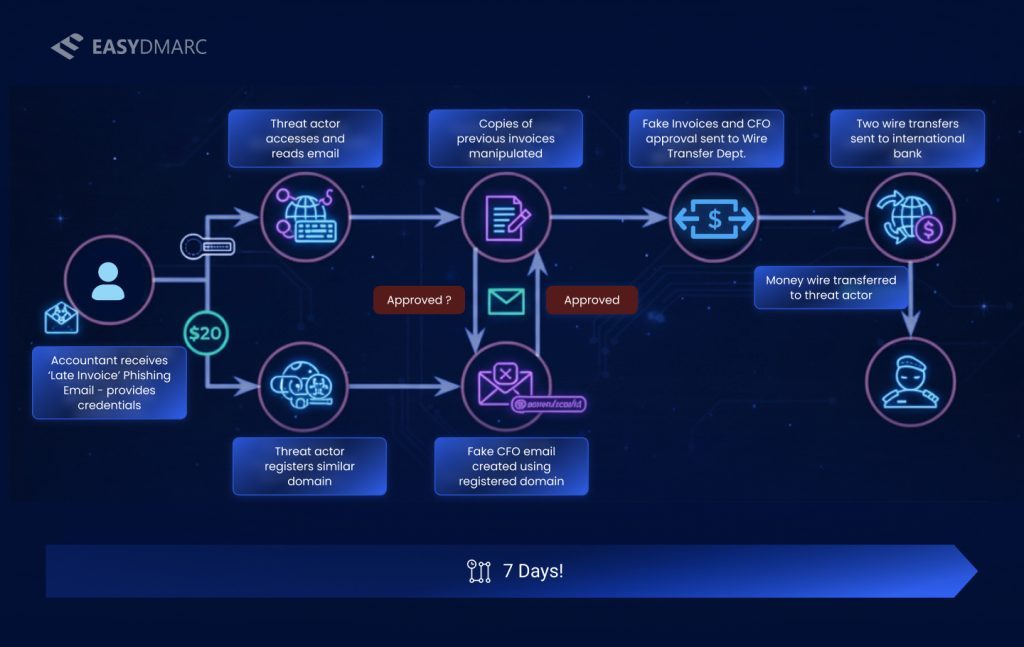
What is a BEC Attack?
BEC attacks are sophisticated email scams that target organizations, often with financial motives or to gain access to sensitive information. Unlike mass phishing campaigns that cast wide, generic nets, BEC attacks are meticulously researched and personalized. Attackers often spend weeks studying their targets’ organizational structures, business relationships, key individuals and communication patterns before launching their assault.
The most common BEC scenario involves an urgent wire transfer request that appears to come from a company executive. When the employee complies, the funds are transferred directly to the attacker’s account and typically moved multiple times within hours, making recovery virtually impossible.
The financial damage from BEC attacks can be devastating. Beyond immediate financial losses, organizations face potential regulatory penalties, litigation costs, reputational damage, and lost business opportunities. In one case, a multinational corporation lost $47 million in a single BEC attack when an executive was tricked into authorizing multiple transfers for a supposed acquisition.
What is a Phishing Attack?
A phishing attack is one in which attackers impersonate trusted entities to trick victims into revealing sensitive information. They typically arrive via email, text messages, or social media, masquerading as legitimate communications from banks, service providers, colleagues, or other trusted sources.
Today’s phishing attacks often feature perfect spelling, convincing logos, and accurate sender information. They create a false sense of urgency, leverage fear or curiosity, and provide seemingly legitimate reasons for immediate action.
The most common phishing scenario involves an email claiming to be from a trusted organization, alerting the recipient to a supposed account problem requiring immediate attention. Recent phishing statistics reveal that the most targeted industry in 2024 was the IT sector. This industry faces greater risk due to its critical role in infrastructure and access to valuable data.
How to Prevent Business Email Compromise Attacks
The best way to prevent BEC attacks is by using a multi-layered approach, combining employee training, multi-factor authentication, and email security protocols.
Employee Training
Regular security training equips employees with the right tools to spot dangerous emails before they do damage. Teaching staff to adhere to email security best practices is a great way to ensure your employees are helping build a security-conscious culture.
Multi-Factor Authentication
Multi-factor authentication (MFA) provides multiple layers of defense through different authentication factors. These typically include something you know (like a password), something you have (such as a smartphone), and something you are (biometric data like fingerprints).
Even if a password is compromised, these additional authentication layers prevent unauthorized access, dramatically reducing the risk of account infiltration. The multiple verification steps create a robust security mechanism that goes far beyond traditional password protection.
Email Security Protocols and Protective Tools
Email security protocols like DKIM (DomainKeys Identified Mail), SPF (Sender Policy Framework), and DMARC (Domain-based Message, Authentication, Reporting, and Conformance) provide critical layers of protection against email spoofing and phishing attempts. These protocols work together to verify the authenticity of email senders and prevent unauthorized use of domain names.
To best identify email security issues, users can use tools like SPF lookups, but to ensure the best possible protection against BEC attacks, organizations must have DMARC properly set up to achieve the most secure email authentication. To do so, users can make use of online DMARC solutions to help them implement the strongest DMARC policies and get support with the continual monitoring of their domains.

How to Prevent a Phishing Attack
To best prevent phishing attacks, as with BEC attacks, we recommend a multi-layered approach, combining technical solutions like DMARC, human awareness including security training, and organizational processes like MFA.
Detecting email security vulnerabilities requires specialized tools such as SPF lookup utilities, DKIM record verification and generation tools, DMARC verification services, and phishing link checkers.
For optimal defense against phishing attacks, organizations should implement properly configured DMARC protocols to maximize email authentication security. Dedicated DMARC solutions like EasyDMARC offer assistance in deploying robust DMARC policies and providing ongoing domain monitoring support.
The Real Cost of Phishing
The damage from phishing attacks extends far beyond initial credential theft, creating long-lasting consequences for organizations that fall victim to them. When attackers gain access to accounts or systems, they can steal sensitive data, including financial information and intellectual property. These breaches often lead to substantial financial loss, with the average cost of a data breach reaching $4.45 million in 2023.
Even more devastating can be the deployment of ransomware across corporate networks, as seen in high-profile cases where companies paid millions in ransom and still faced weeks of operational disruption. The repercussions continue to ripple outward as cybercriminals establish persistent access for extended campaigns, sometimes maintaining hidden footholds for months before being detected. Using compromised accounts, attackers frequently target an organization’s partners and customers, exploiting established trust relationships to spread their reach.
This cascade effect severely damages brand reputation and erodes customer confidence, as demonstrated when major retailers experienced phishing breaches that led to measurable customer churn and required expensive brand rehabilitation campaigns. The combined impact of regulatory fines, litigation, remediation costs, and lost business opportunities often transforms what seemed like a simple email attack into an existential threat for many businesses.
The Impact of all Email-Based Threats
The financial impact of email-based threats has reached unprecedented levels. According to the FBI’s Internet Crime Complaint Center, BEC scams resulted in over $2.77 billion across 21,442 reported incidents in 2024 alone. What makes a BEC attack different from a typical phishing email is its highly targeted nature. While phishing often involves mass distribution of generic threats designed to lure people in, BEC attacks specifically impersonate executives or trusted partners to target individuals with financial authority. The 2023 Verizon Data Breach Investigations Report also revealed that phishing attempts increased by 18% year-over-year, with 74% of breaches in financial services involving phishing as the initial attack method.
Organizations can significantly strengthen their security posture through a combination of employee awareness training and effective security controls. Teaching staff how to identify suspicious emails represents a critical first line of defense, while implementing email authentication protocols provides essential protection.
DMARC solutions for businesses, like those provided by EasyDMARC, help organizations verify sender legitimacy, prevent domain spoofing, and block unauthorized emails before they reach employee inboxes, effectively neutralizing these threats before they can exploit various vulnerabilities. This multi-layered approach not only protects sensitive information but also preserves business continuity, shields organizational reputation, and maintains the trust that customers and partners place in your digital communications.
The Evolution of Phishing
Phishing has been around since the early 90s, and is the more common of these two types of attacksSince their inception in the 90s, phishing attacks have progressed significantly. Early attacks often contained obvious red flags like poor grammar and unlikely scenarios. Since then, cyber criminals have refined their tactics, creating more convincing messages that mimic legitimate organizations with increasing accuracy.
Modern attacks often include spear phishing, which targets individuals through the use of personal relevant information, clone phishing, which replicates legitimate emails but replaces attachments with malicious versions, vishing, involving voice phishing via phone calls, and pharming, which redirects website traffic to fake sites without user interaction.
Today’s most sophisticated phishing attacks employ AI-generated content that can adapt to targets in real-time, creating highly personalized and convincing communications. According to SlashNext’s 2023 State of Phishing Report, AI-enhanced phishing attacks increased by 1,265% in 2022 alone, with attackers using machine learning to craft increasingly convincing messages.

Recent Trends and Emerging Threats
Phishing threats continue to evolve at a rapid pace. Recent trends include:
- QR Code Phishing: Attackers embed malicious QR codes in emails that direct victims to credential-harvesting sites
- MFA Bypass Techniques: Sophisticated phishing kits that can intercept and replay authentication tokens in real-time
- AI-Generated Content: Using large language models to create highly convincing and contextually appropriate phishing messages
- Collaboration Platform Targeting: Focused attacks on workplace tools like Microsoft Teams, Slack, and Google Workspace
EasyDMARC Can Prevent BEC Attacks and Stop Phishing
As cyber threats continue to evolve, organizations must understand the nuances between BEC and phishing attacks to build more effective defenses. Both attack types exploit human trust and communication habits, but BEC attacks stand out for their precision, research, and high financial stakes, while phishing typically relies on volume and opportunism. Regardless of the method, email remains the most exploited vector, making email security a critical priority.
At EasyDMARC, we equip businesses with DKIM Checkers and other tools needed to identify, categorize, and neutralize both BEC and phishing threats, as well as countless other attacks. By implementing email authentication protocols like DMARC, SPF, and DKIM (and providing quality of life tools like DMARC record generators)organizations can verify sender identity and prevent domain spoofing.
Our platform also offers powerful tools to help users detect weaknesses and take action before attackers can exploit them. Features like real-time alerting and aggregate reporting give organizations the visibility and agility needed to respond quickly and decisively to suspicious activity.
Looking ahead, phishing attacks continue to rise year upon year, becoming increasingly targeted and convincing. Meanwhile, BEC attacks are growing in sophistication and financial impact. The most effective way to stay ahead of these evolving threats is by adopting a proactive, layered defense strategy that includes email authentication. With the right tools, policies, and training in place, organizations can significantly reduce their exposure and build long-term resilience against the next wave of email-based attacks.
Frequently Asked Questions
Business Email Compromise (BEC) and phishing both use email as the entry point, but they differ in intent, scope, and technique.
BEC attacks are highly targeted schemes where cybercriminals impersonate executives, vendors, or other trusted contacts. The goal is to pressure employees in finance or HR to transfer money or share sensitive data. These attacks rely on social engineering and persuasion, often without links or attachments, which makes them more difficult for email filters to detect.
Phishing attacks are broader and less personalized. Attackers send mass emails designed to trick recipients into clicking fake links, downloading malware, or entering credentials into fraudulent websites. Phishing campaigns focus on volume, hoping that even a small percentage of victims will respond. BEC campaigns focus on precision, often leading to larger financial losses from only a few successful attacks.
BEC attacks almost always involve impersonation of a company employee, so they often begin with an email from an attacker impersonating someone at the company. In some cases, the attacker will target the company’s accounts payable department with an email containing a malicious link or attachment. Once the link is clicked, the attacker can gain access to the accounts payable email, making stealing money much easier.
Here is an example of what an email from a BEC attack may look like.
“Hi [Employee Name],
I need you to process an urgent payment of $100,000 to [Vendor Name]. This payment is time-sensitive, and we need it completed by the end of the day. Please wire the funds to the following account:
Account Number: 1234567890
Routing Number: 987654321
Bank Name: [Fake Bank Name]
Let me know once it’s done. This is very important.
Best,
[CEO Name]
BEC attacks are harder to detect because they rarely include the typical red flags found in phishing emails, such as malicious links, suspicious attachments, or obvious grammatical errors. Instead, they rely on social engineering and impersonation, often using real or compromised email accounts to appear legitimate. This makes automated security filters less effective, leaving employee awareness and authentication protocols as the main defenses.
Business Email Compromise (BEC) attacks typically target specific individuals within an organization who have access to financial transactions, sensitive company data, or the ability to authorize actions such as fund transfers. The attackers often focus on individuals who are more likely to be tricked into complying with requests that appear legitimate.
BEC involves attackers impersonating executives or trusted partners to trick employees into transferring money or sensitive data. It’s highly targeted and often financially motivated. In contrast, EAC (Email Account Compromise) occurs when an attacker gains unauthorized access to an individual’s email account to steal information or monitor communications. While BEC focuses on financial fraud, EAC is generally more about unauthorized access and data theft.
DMARC (Domain-based Message Authentication, Reporting, and Conformance) helps protect against BEC and phishing by verifying that incoming emails are sent from authorized domains. When combined with SPF and DKIM, DMARC prevents attackers from spoofing legitimate email addresses, a common tactic in both attack types. With a properly enforced DMARC policy, organizations can block fraudulent emails before they reach employees’ inboxes and gain visibility into suspicious activity through reporting tools.





