Email is a commonly used communication tool in almost all business practices. Unfortunately, it also serves as a gateway for scammers to reach you. Phishing scams might seem like something you can detect right away. However, cybercriminals can easily trick you into providing personal information without even knowing it.
According to the FBI, cybercriminals scammed $57 million out of victims in 2019 alone. Phishing schemes may use a combination of fake websites and emails to lure victims into forking over sensitive data, which can lead to identity theft, financial loss, and more. The best way to protect yourself is to learn how to recognize a phishing attack and establish a set of protocols to protect against phishing. Here’s how.
What Are Email Phishing Attacks and Scams?
Phishing emails are emails from scammers that look like they are from a legitimate source. Scammers may have done extensive research on you or your company. And they use this information to trick you into trusting them. Thus, phishing email attackers may communicate with you several times before asking for sensitive information, such as sending funds to a fake account.
Phishing emails may also include CEO fraud, which occurs when the scammer pretends to be the CEO of a trusted company in an attempt to gather information or have an employee wire money to a fake account. Also, phishing emails may ask you to download malware that can be used to steal your information. Although phishing emails can be hard to spot as they appear to come from legitimate sources.
Phishing emails or text messages are designed to look like they are from a company that you already know and trust, such as a bank, social networking website, online payment spot, an online store, or a bank. They often tell a story or use a catchy opening phrase to get you to open the email and click on an attachment or link. Phishing emails may say that they have noticed suspicious activity or invalid log-in attempts from your account. Moreover, they may also claim that there is a problem with your payment or your recent activity.
Other tactics that scammers may use include the following:
- You may be asked to confirm personal information
- Also, you may be informed that you are eligible for a refund of some sort
- You may be offered a coupon for free things
- Or you may be asked to click on a phishing link to make a payment or accept funds
- Scammers may send a fake invoice from a company that you trust
For example, a major bank that you do business with may email you with a subject line that states, “Immediate Attention Needed – Problems With Your Account.” If you open the email, the body of the text will claim that there is a problem with your account and you need to validate it to protect your information. Scammers can send this email to thousands of people. Some may believe that the email is real and they will click on the link in the email.
However, most people do not notice that the link takes them to a website that does not match the institution it claims to be. In some cases, the website URL may only partially match the said website. The user will be taken to a bogus site that looks like the real thing. From here, spammers ask to enter personal information, including name, address, account number, online banking username and password.
Once you enter this information, the hacker has everything they need to steal your money. They can use it to hack into your private or business accounts and send emails to your clients. In many cases, phishing emails will entice an employee to wire money into a fake account by pretending to be the CEO of the company. They may even send an email from the CEO’s account, requesting that funds be sent to an account in a different country.
Spear phishing
Spear phishing is a more sophisticated type of attack that involves sending an email to a specific person. Cybercriminals usually have information about the person they are sending the email to. Including their job title, name, place of employment, email address, and other specific information about their job. Spear phishing usually targets an employee in hopes of getting them to provide their username and password or by making a wire transfer to a fake account. Sometimes, cybercriminals target top executives: they may ask for sensitive documents, such as W2’s and tax return documents.
How To Recognize A Phishing Email
Scammers are always updating their tactics. This can make it hard to identify a phishing email attack. For example, many scammers have found a way to ensure that their emails get past your spam folder and make it to your inbox. They may also outsmart other security checks. However, there are several things you can look for to recognize a bogus email or text.
Many phishing emails claim to be from financial institutions, such as banks, credit card companies, and online payment methods, such as PayPal. They may also come from online stores that you commonly do business with. In many cases, a hacker will do extensive homework on a company to learn how to gain your trust. They may know who you do business with and what platforms you use to transfer money.
If you receive an email from a bank or online company, carefully examine it to determine what they are asking you for. And if the email asks you to verify your account information, provide sensitive data, or click on a link that takes you to another website, then it may be a phishing scam.
Some of the most common phishing attacks and scams may use the following wording in their emails:
Phony communication from an auction service, online payment, or internet service provider claiming that there is a problem with your account. These emails usually ask that you click on a fake website to verify your personal information.
Emails that claim you violated the Patriot Act. These emails claim to be from the Federal Deposit Insurance Corporation (FDIC) and they state that the FDIC will not verify your account because it suspects that you have violated the USA Patriot Act. The scammer will request that you provide information to verify your identity by clicking on a link that takes you to another webpage, which is usually fake: it will steal your identity.
Emails from an IT department, even within your own company, that attempt to steal your password and other information. Hackers may pose as someone from your company and ask you to verify information or send your login information. Once they have this data, hackers can gain access to your company’s bank accounts, email, sensitive data, and more.
You can usually detect a phishing email by paying attention to the characters in the fake domain. For example, some fake accounts will send you an email with an “r” and “n” next to each other instead of an “m.”
They may also use an organization’s name in one part of the domain in hopes of identifying with the organization that it’s trying to duplicate. For example, you may get an email from [email protected]. The hacker hopes you will see the “PayPal” in the email address and assume this is a legitimate domain. Always pay attention to the domain’s address.
How To Protect Yourself From Phishing Attacks
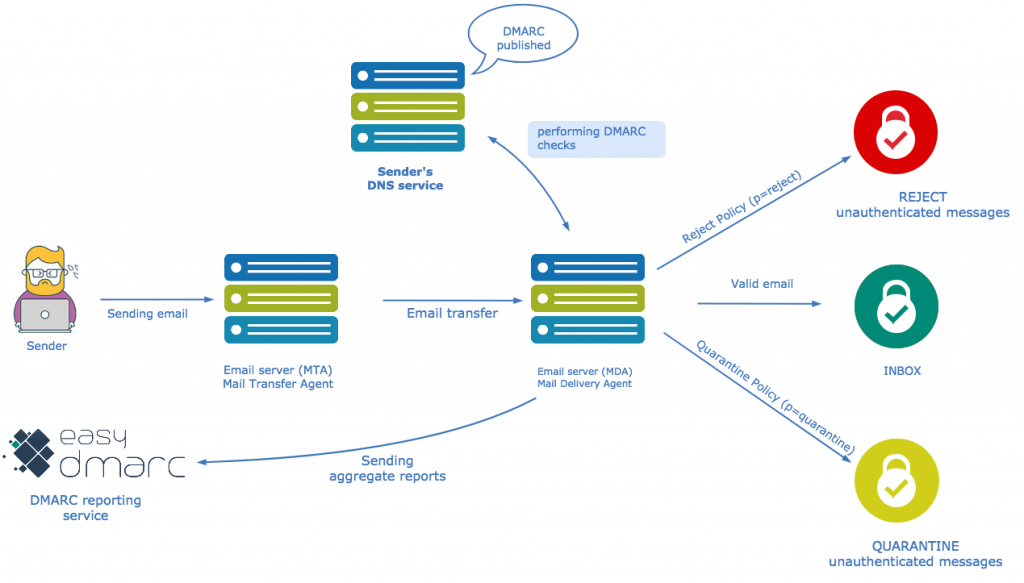
The best way to protect yourself (and your business) from phishing scams from your domain is to implement DMARC email authentication protocols on your domain. DMARC with a reject policy stops cybercriminals from sending you fraudulent emails from your domain. It also stops them from sending fraudulent emails to your business partners, employees, and customers. It protects against data, customer, and financial loss. As an email authentication strategy, DMARC takes Domain Keys Identified Mail (DKIM) and Sender Policy Framework (SPF) standards and enhances them, ensuring that emails that make it through to your inbox are legitimate.
DMARC puts all emails that come through to your email through a test. It works in two ways. First, it uses SPF to make sure the domain matches both the ‘return-path’ and ‘header from’ and validates the sending source. Next, it ensures that the ‘header from’ matches the DKIM signature. If these items do not match up, then the emails will not be sent to your inbox.
You can also use DMARC to tell your receiving email providers how to handle all emails from your domain. You can use DMARC only to monitor all mail statuses regardless if it has passed a check or not, send failed emails to your spam box, or reject failed emails altogether. As a result, DMARC reduces the risk of any phishing emails making it to your or your partners, customers’ inbox where hackers have the potential to steal information or money. Follow the link, to learn how to implement DMARC with EasyDMARC.
Use our scam website checker to filter out phishing domains.
What To Do If You Receive A Phishing Email
If you’re suspicious about an email, do not open it or click on any links that it provides. Instead, call the company that is emailing you and inquire about the problem at hand. Never respond directly to the email as you may be unintentionally handing over sensitive data to your attacker. And never provide sensitive information to a website if you’re skeptical.
Conclusion
Email phishing attacks might be something you think you can detect on your own. However, due to sophisticated approaches and ever-changing tactics by hackers, it’s harder than you think to protect your information. A phishing email occurs when a cybercriminal sends an email from a domain that looks like a legitimate source and acquires personal data, such as your username, passwords, and financial data. Phishing emails can scam businesses out of millions of dollars.
Never click on a link from an email that seems suspicious. You can protect against phishing emails by utilizing DMARC email authentication protocols on your domain. DMARC acts as a traffic cop to test every email that makes it through to your inbox. If it fails a check, you can instruct your domain to allow the email to come through, reject it completely, or send it to your inbox. DMARC helps limit the possibility of phishing attacks by protecting your domain against fraud.