Internet use continues to expand among the global population. Today, the world wide web is vital to millions of households and businesses. This enormous growth has made information security a burning topic in recent times.
New cyberthreats are discovered every day, and the need for organizations to implement sophisticated security measures is more vital than ever. One of the latest cyberattacks is called tabnabbing.
While the human factor is often the weakest link in a cyberattack, tabnabbing doesn’t need users to perform any action, i.e., clicking a malicious link or downloading an attachment.
In this article, we’ll walk you through how to prevent tabnabbing.
But first, you need to understand what it means. So, what is tabnabbing?
What is Tabnabbing?
Tabnabbing is a social engineering attack in the phishing category. Essentially, it manipulates inactive web pages left open in your browser. This attack redirects a legitimate page to an attacker’s malicious website. Like other phishing methods, a tabnabbing attack aims to trick users into submitting their login credentials and other sensitive information.
Let’s look at a tabnabbing example to give you a better understanding.
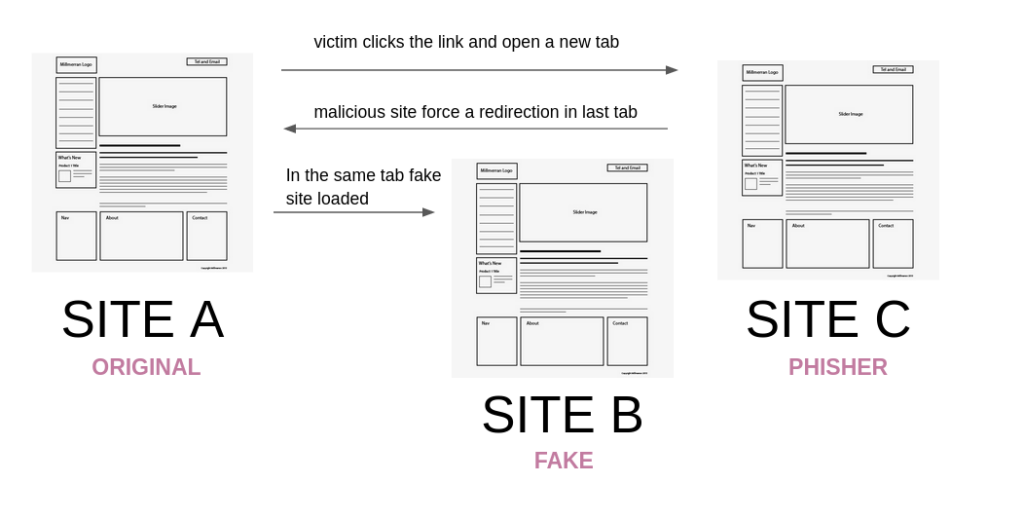
Suppose you’re on Site A, a social media or blog page, and you click on a link with a target = “_blank” that redirects you to Site B.
From Site B, an attacker then redirects Site A to a malicious page on Site C, which can be a login page that looks identical and legitimate to the one of Site A.
What is the Same-Origin Policy?
Let’s discuss what the origin is to understand this policy better. If the host, port, and protocol are similar, the URLs are from the same origin. Most web browsers consider two URLs to be from different origins if any of these three elements are different.
Same-Origin Policy is a rule enforced by web browsers that manage data access between web applications and websites. With this policy, any website can access other web pages’ Document Object Model (DOM).
The purpose of the Same-Origin Policy is to separate websites from each other. For instance, when you’re accessing Facebook.com, the webpage won’t be able to access your bank login page that’s open on another tab. This policy helps isolate malicious pages, thus, reducing possible attack vectors.
Tabnabbing Example
There’s no denying that opening numerous tabs is common among users when multitasking. This makes you more susceptible to a tabnabbing attack. When you have several tabs open, it’s easy for pop-ups to display without your knowledge.
You might even think you opened the page yourself. For instance, let’s assume you have your bank page open among your tabs.
- First, the malicious tab redirects the original bank page to a fake one with the same login interface.
- For security purposes, sensitive sites like your bank page always log you out when you’re inactive for some time. So when you tab back to your bank page, you’re presented with a fake login page.
- You then assume you were automatically logged out and re-enter your credentials.
- The tabnabber now has your sensitive bank login details—all without your knowledge.
How Do Tabnabbing Attacks Work?
The first step to preventing an attack is to understand how it works. In the case of tabnabbing, there are different ways a malicious page can get the window handle to a legitimate website. Below are some of the common ways:
The “Malicious Page” Opens a Window
An attacker can create a malicious page that opens a window on your web browser via the window.open() method. This method opens a resource on a new or existing browsing tab.
The “Good Page” Opens a Window (Reverse Tabnabbing)
Another way to carry out a tabnabbing attack is when the legitimate page opens a window using the window.open() method. The attacker then uses the malicious web page to get a window handle to the legitimate website through the window.opener method.
In most cases, navigation of the opener window is possible, meaning that the open page can access a URL from the original window. This makes phishing possible as an attacker can replace the original window (i.e. the “good” page) with a phishing website (i.e. the “malicious: page).
Reverse Tabnabbing Through Links
When a user clicks on a link with a target = “_blank”, an attacker can redirect the user to a malicious site under their control. Once you access the malicious page, it can control the original page using the window.opener object.
The attacker then changes the location of the original page using the window.opener.location so it can replace it with a fake website that resembles the original one.
Reverse Tabnabbing Through Frames
Another way an attacker can execute reverse tabnabbing is through frames. A website can load another web page in an iframe. Many ads work in this way. As such, a malicious page can redirect the parent page using the window.parent property.
Why is Tabnabbing Efficient?
Unlike with other phishing methods, preventing tabnabbing attacks can be daunting. The victim doesn’t need to perform any action like clicking a link or downloading an attachment. Web browsers can navigate through a page’s origin in static tabs, making the attack even more efficient.
When we use a web browser, we often open numerous tabs simultaneously and keep them open to switch between pages. When we leave a page inactive for a long time, an attacker can gain control and replace it with a fake replica.
How to Prevent Tabnabbing Attacks
Tabnabbing is a sneaky phishing scam that an attacker can execute in your browser without your knowledge. That doesn’t mean you’re helpless, though. On the contrary, you can prevent tabnabbing by implementing the following measures:
Always Check the Domain
Before entering your login details, make sure the domain is legitimate and keep an eye out for any strange or suspicious-looking additions to the URL. Familiarize yourself with important or frequent domains you use to quickly identify any anomalies.
Use Mobile Apps Instead of Your Mobile Browser
Mobile browsers are notoriously targeted by tabnabbers. If you need to login into your email, e-wallet, bank, or e-commerce store account, rather use the trusted app wherever possible.
Implement a Cross-Origin Opener Policy
The Cross-Origin Opener Policy is a new security feature available in most browsers. This policy allows you to ensure that a top-level document doesn’t share a browsing window or tab with cross-origin documents.
The Cross-Origin Opener Policy or COOP restricts the ability to alter the document.domain. Being able to alter the document.domain is a security loophole in the Same-Origin Policy we discussed earlier. Unlike COOP, this security flaw makes it easier for attackers to execute a tabnabbing attack.
Conversely, the COOP isolates your documents, preventing potential tabnabbers from accessing top-level windows and opening malicious sites in your browser. New tabs or windows opened via the window.open() property won’t be able to attack the system, either.
This policy is now available in popular browsers like Google Chrome and Mozilla Firefox.
Set the rel=”noopener” Attribute to Your Links
If you want to link your website to other pages in new windows, the best practice is to include the rel=”noopener” attribute to your links or a tag. Find an example below:
<a href=”https://www.example.com” rel=”noopener noreferrer”></a>
How does the “noopener” attribute work?
The “nooppener” attribute instructs the web browser to navigate to the target site without granting the new browsing context access to the parent document that opened it. It sets the window.opener to “null.”
This is crucial when opening untrusted sites to prevent tampering with the original web page via the window.opener property.
Though the “noreferrer” is not related to tabnabbing, it’s the best practice, and you can also adopt it. The “noreferrer” prevents data from a user browser’s URL from leaking to other websites.
Sandbox Your Frames
An excellent preventive measure against tabnabbing from websites you load in the iframe is to sandbox the frame using the sandbox attribute as indicated below.
<iframe sandbox=”allow-scripts allow-same-origin” src=”https://www.example.com”></iframe>
The sandbox attribute is an HTTP Content-Security-Policy (CSP) directive that restricts a page’s actions (including popups), enforces a same-origin policy, and prevents the execution of scripts and plugins.
So when you open a new tab in an iframe, the sandbox prevents the new window from redirecting its parent page.
Implement an Isolation Policy
One recent browser’s feature is the fetch metadata—an HTTP request header that provides the browser with additional information about the context from which the request originates from.
With this request header, you can implement an isolation policy that allows external sites to only request data that are intended for sharing, and used appropriately. This isolation policy is an effective security measure to prevent cross-site threats like tabnabbing attacks.
This policy is not yet supported by browsers like Safari and Firefox. But you can still implement it in a fully backward compatible way to enjoy its benefits on unsupported browsers.
Final Thoughts
Tabnabbing is a dangerous threat which can be difficult to prevent. However, we’ve discussed simple security measures you can implement to protect your web browser from tabnabbers.
Ensure you implement a cross-origin opener policy and add the rel=”noopener” attribute to the links on your website. Also, don’t forget to implement a resource isolation policy and add sandbox attributes to iframes on your website.
As with all other phishing types, cybercriminals can target anyone. So organizations must educate their employees to identify and defend against any form of phishing attacks.