Cyber threats are everywhere, and they evolve non-stop. Businesses these days need to actively protect company, employee, client, and partner information no matter what industry they’re in.
Hackers are generally after industries they can exploit for large financial gain and personal information. The more data you store, the higher the risk of attracting the attention of cyber threat actors.
We’re starting a set of articles consisting of 5 modules that will dwell on:
- Who can be after your company information?
- What methods, tactics, and techniques do they use?
The first module introduces the basics of threat and threat actor-related terminology and describes the notions of a cyber attack, with a simple email example.
Cyber Threat Actors: Main Terms You Need To Know
Before we go on into threat actors and their tactics, here are a few terms that will help you navigate the topic.
- Threat actor: A person, group, or entity representing a threat to a company’s cyber security.
- Cyberattack: The stealing, modification, or destruction of a company-owned data or asset.
- Threat: Any activity that puts a company’s data or assets in harm’s way.
- Vulnerability: A weakness that could be exploited or triggered by a cyber threat actor.
- Loss: The negative effect due to compromised sensitive information in an organization.
- Cyber risk: The probability of a threat, which can cause vulnerability exploitation and compromised data (loss).
What’s a Cyber Attack: An Example
One of the widespread attacks is the social engineering type, where somebody from the organization needs to fall prey to a malicious URL or an attachment. These are usually sent in an email to unsuspecting facilitators.
A vivid example of a social engineering attack is the Dyre Wolf campaign, which has stolen more than $1 million from targeted companies using various Dyre Trojan malware. While widespread viruses attack individual users, the uniqueness of social engineering attacks is their company-oriented nature. As a result, large businesses continually lose millions of dollars every year.
Here is how it works.
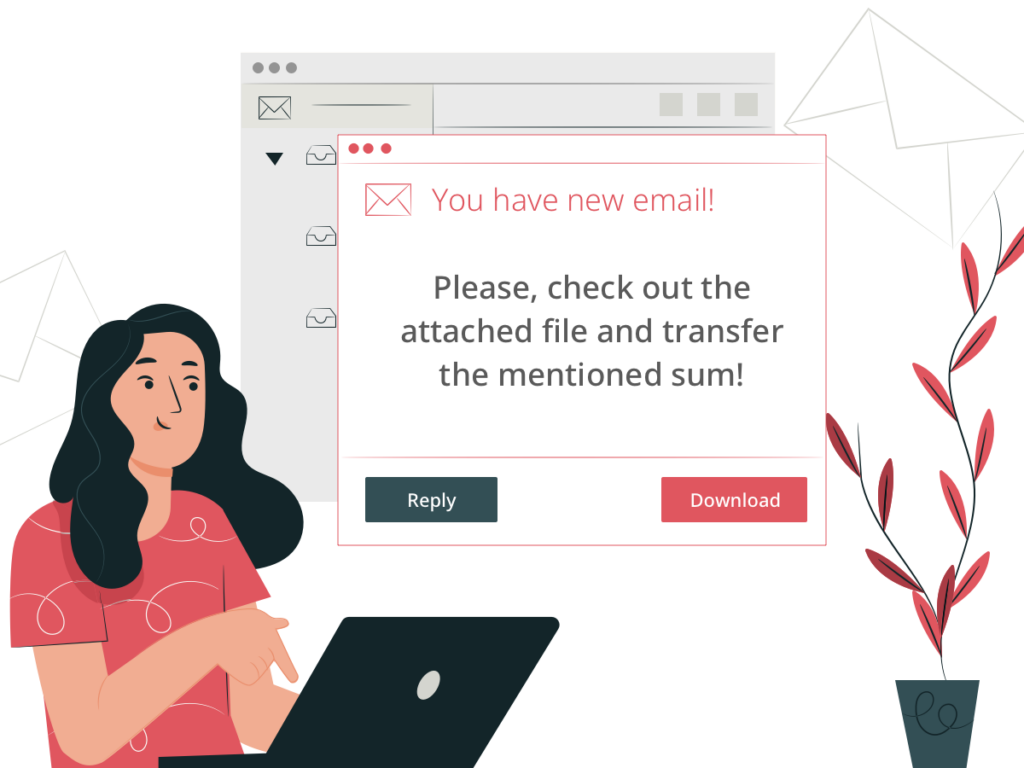
Caroline works at an IT company as an accountant. It’s almost lunchtime, and she gets an email from the company’s CEO saying “Please, check out the attached file and transfer the mentioned sum.”
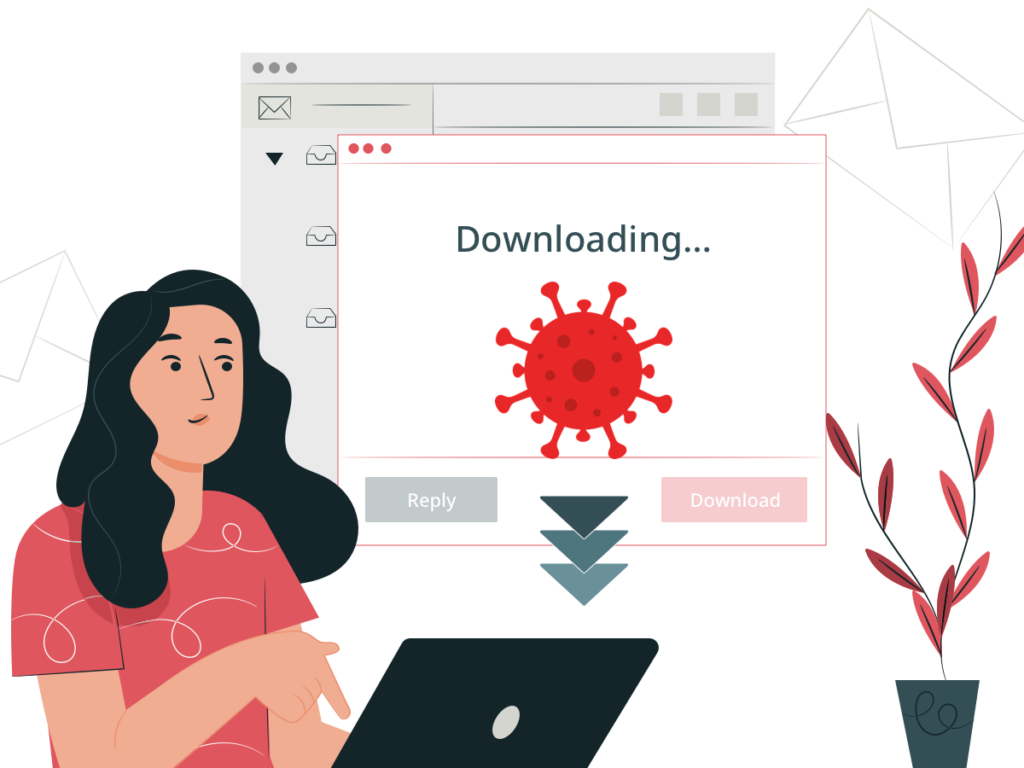
Assuming that the real CEO sent the email, she downloads the file. While she’s reading the document, malware loads onto her computer in the background. As a result, the cybercriminal gets a backdoor to Caroline’s computer.
The next step is to mislead the prey with an error message during login. Something along the lines of the following pops up: “There was an issue with your login. Call us at 503-3333”.
Trying to solve the problem, Caroline phones the number, and somebody on the other side of the line, a fake bank employee, asks her to verify the bank login details. With the information gained, the cybercriminal can access the company’s account and manipulate it as they wish. Namely, they can steal money or even change the password, robbing the company of access to their assets.
Then, the cyber threat actor will likely distract Caroline with a denial of service message, stalling her until they finish the attack.
That is all for our first module! We’ll continue discovering more about cyber threat actors in the module 2.