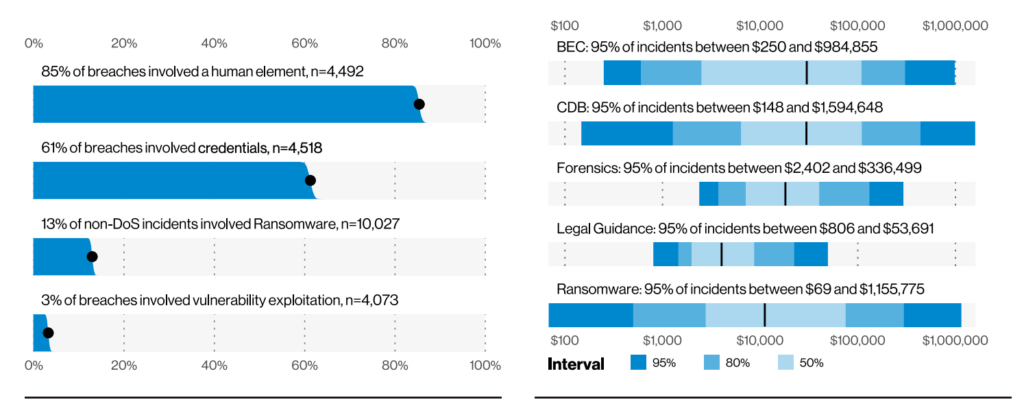
Social attacks as a pattern have continued to increase since 2017, with Business Email Compromise (BEC) breaches doubling again since last year
The DBIR (Data Breach Investigation Report) by Verizon reveals the attack methods used by hackers, the latest scam tactics, and malware incidents. The recent shift to WFH has escalated the hacking tactics to cause downtime or launch ransomware attacks on organizations.
Initiating the zero-trust approach is not enough to tackle ransomware attacks.
The DBIR and publishing actual attack details by different organizations can prepare us for future incidents. Spreading awareness and organizing training sessions with discussions of the latest phishing and social engineering attacks can help reduce ransomware attacks. Analyzing attacks and sharing every minor detail of attacks or outages is an unplanned investment resulting in better risk mitigation and minimization. Here are some interesting insights on Verizon’s 2021 DBIR to put the organization on the right track.
- After DOS, social engineering tactics followed an alarming rate of social attacks and credential theft (61%).
- The default, stolen, or vulnerable credentials targeted in the web application layer exploited customer profiles and led to security breaches of cloud and web applications.
- This DBIR highlights humans as the weakest and most vulnerable link for the occurrence of security breaches at the rate of almost 85%. Phishing was present in 36% of breaches, up from 25% last year. Business Email Compromise (BEC) was the second-most common form of Social Engineering. This reflects the rise of Misrepresentation, which was 15 times higher than last year.
- Financially motivated attacks involved basic web application attacks, system intrusion, social engineering, and DOS.
- Compared to previous years, an increase of 26% was observed in the malware attacks with the latest hacking tactics involving social and physical environments.
- Misuse of actions also increased this year due to the initiation of social engineering tactics where users exploit their legitimate access to launch cyber attacks. The intentions behind the misuse of actions are financial benefits or revenge games.
- Insufficient training and/or the lack of security workshops or awareness sessions for employees directly correlates to the level of employee vulnerability to mistakes and errors. This empowers hackers.
- The attack vectors in breaches mentioned this year are web applications, VPN, and desktop sharing.
- Out of all the assets in an organization, such as networks, media, and employees, web servers are targeted most by hackers.
- With the WFH shift employees made, user and personal devices became the most breached assets, while web servers immediately followed. These breaches mostly occurred due to business email compromises, clicking on spam links, or social engineering attacks.
The DBIR highlights the misconfigured clouds and vulnerabilities in web applications, increased DOS, and web server downtime. An unexpected increase in privilege misuse was up 98%, and cyber espionage is up 66%.
In your estimation, what makes your organization the least prepared if a cyber-attack occurred?
- Not having enough knowledge and updates on top vulnerabilities
- Less in-house expertise to launch a remedy against cyberattacks
- Insufficient details of critical data and assets to prioritize when under attack
- Inefficient vulnerability assessment and penetration testing tools