Email authentication is a verification method that helps email servers determine the legitimacy of an email message to confirm that you, the sender, are who you say you are. This mechanism is used to prove that an email message isn’t forged, thereby blocking any fraudulent mail.
Even though email is now a key communication channel for organizations, security was never a built-in feature. Hackers leverage these email security weaknesses through phishing, domain spoofing, or spam campaigns to steal sensitive data such as login credentials and other personally identifiable information. Email authentication is one of the most effective security measures to prevent bad actors from exploiting organizations’ email domains.
This article discusses how email authentication works, its methods and benefits, and Email Authentication as a Service.
How Does Email Authentication Work?
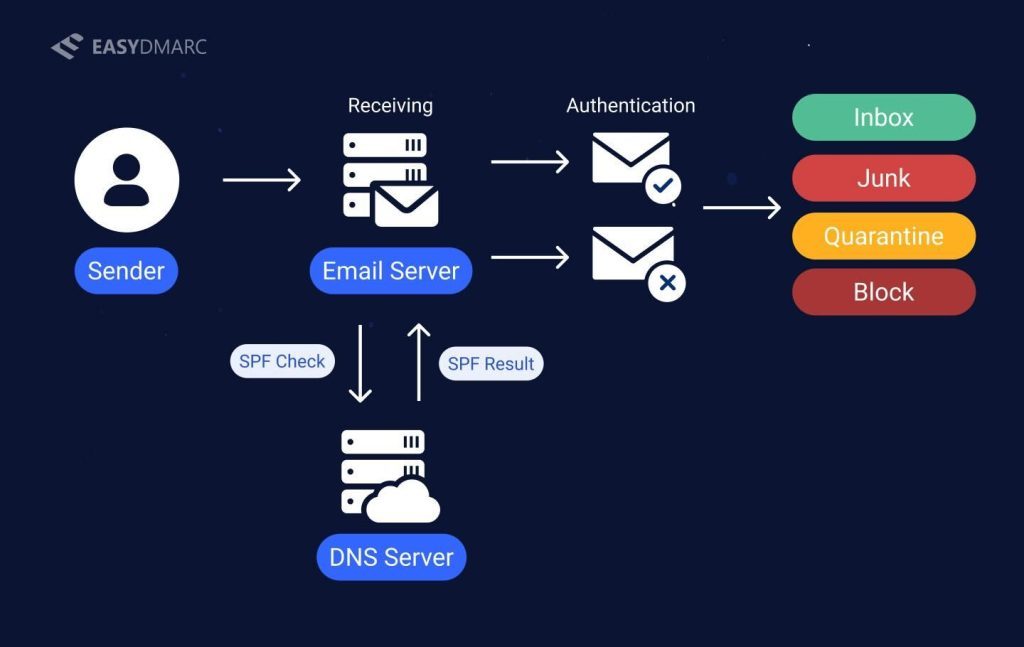
Email authentication is the process that enables email providers to verify whether a message truly comes from the domain it claims to represent. It establishes trust between the sender and the recipient by checking if the email was sent from authorized sources and wasn’t altered during delivery.
When a domain owner sets up authentication protocols, they publish specific policies and cryptographic keys in their Domain Name System (DNS). These policies define which mail servers are permitted to send messages on behalf of the domain.
Here’s a simplified flow of how it works:
- Policy creation: The domain owner implements authentication protocols such as SPF, DKIM, and DMARC, each serving a specific function in validating emails.
- Policy publication: The policies are stored as DNS records, making them publicly accessible for receiving servers to check.
- Verification on receipt: When a recipient’s server gets an email, it runs the message against the published authentication policies.
- Action based on results: Depending on whether the email passes or fails these checks, the receiving server delivers it to the inbox, places it in spam, or rejects it altogether.
Because both the sender and the receiver must follow these rules consistently, email authentication protocols form the backbone of secure email communication. Without them, domains remain vulnerable to phishing, spoofing, and other fraudulent tactics.
What Are the Email Authentication Methods?
The main email authentication methods or protocols are SPF, DKIM, and DMARC.
SPF
SSPF or Sender Policy Framework is an email authentication mechanism that allows you to specify the sending sources or IP addresses authorized to send messages on your domain’s behalf. These senders are listed in your SPF record, a TXT record in your DNS, and can be verified using a DNS record checker.
DKIM
DKIM, or DomainKeys Identified Mail, is an another email authentication standard used alongside SPF to provide additional protection against attacks. DKIM allows you to include a digital signature in the email header of every message using a private cryptographic key to confirm the origin and authenticity of the message.
DMARC
DMARC, or Domain-Based Message Authentication, Reporting, and Conformance, is an email authentication protocol that leverages SPF and DKIM to verify whether a message is legitimate.
DMARC covers the shortfalls of SPF and DKIM by verifying that the return-path address and the DKIM signing address match the “from:” address the recipient sees. It also tells receiving servers what to do with messages that fail these authentication checks.
BIMI
BIMI, or Brand Indicators for Message Identification, is an innovative email standard that enables brands to display their logo beside their message. With BIMI, only authenticated emails can have a brand logo, so recipients know the message is legitimate.
Who Needs Email Authentication?
Any organization that uses email is at risk of phishing or spoofing, but these types of organizations are particularly at risk:
- E-commerce businesses: Protect order confirmations, shipping updates, and promotional emails so customers don’t fall for fraudulent look-alikes.
- Marketing teams: Improve campaign deliverability and ensure brand emails are trusted, not filtered into spam.
- IT and security departments: Safeguard internal and external communications from impersonation attempts.
- Large enterprises: Defend high-visibility brands that are frequent targets of cybercriminals.
- Small and mid-sized businesses (SMBs): Reduce risk without heavy technical overhead using simple, user-friendly tools.
- Nonprofits and educational institutions: Protect donor, student, and member communications while maintaining trust in their mission.
By deploying SPF, DKIM, and DMARC for email authentication, organizations across all sectors validate legitimate email traffic and block attackers. Adding BIMI further strengthens trust and builds brand recognition directly in recipients’ inboxes.

Benefits of an Authenticated Email
Email authentication directly impacts how your messages are delivered, perceived, and trusted. By validating your emails with SPF, DKIM, and DMARC, you protect your organization from threats while also creating a stronger, more reliable communication channel with customers and partners.
Fraud Prevention
Emails don’t have built-in security, so bad actors can leverage them to trick victims into releasing sensitive data that can be used for fraudulent activities. With DMARC implementation, you can confirm the authenticity of your messages to prevent email fraud.
Brand Image Protection
Building a reliable reputation with your customers takes years, but one phishing campaign using your domain can erode that trust in minutes. Email authentication helps stop cybercriminals from impersonating your brand and misleading your customers.
Enhanced Email Deliverability
Cybercriminals send non-stop malicious messages daily. Internet service providers (ISPs) filter out suspicious messages, which commonly lack email authentication. With DMARC, ISPs can validate the authenticity of your message from the get-go, so your messages avoid spam folders.
Stronger Domain Reputation
Mailbox providers reward domains with consistent authentication by treating them as trustworthy senders. This improves long-term deliverability and ensures legitimate messages are not mistakenly flagged as spam.
Regulatory and Security Compliance
Many industries require organizations to demonstrate strong email security measures. Implementing SPF, DKIM, and DMARC supports compliance with these requirements and reduces legal or financial risks.
Customer Confidence
When recipients know your messages are authenticated, they are more likely to engage with them. This builds ongoing confidence in your communications and helps establish lasting customer relationships.
When your mails are authenticated, they’re usually sent directly to the receiver’s inbox. This can improve your click and open rates, thereby increasing conversions. With a better deliverability rate, your domain reputation improves, and your campaigns are more successful. Moreover, fraudulent messages that exploit your company’s name are automatically blocked.
Email authentication is vital for any business that relies on email marketing and communication. Ignoring email authentication can cost you time and sales.
How Can I Implement Email Authentication Protocols like SPF, DKIM, and DMARC?
Implementing email authentication begins with configuring DNS records for your domain and ensuring each protocol works together to verify your messages. While the setup may seem technical, breaking it into steps makes the process manageable.
SPF (Sender Policy Framework)
Start by creating an SPF record in your domain’s DNS. This record specifies which mail servers are authorized to send emails on behalf of your domain. Keeping this record accurate and updated is essential, especially if you use multiple third-party email providers.
DKIM (DomainKeys Identified Mail)
Next, configure DKIM by generating a pair of cryptographic keys. The private key signs outgoing messages, while the public key is published in your DNS as a TXT record. Receiving servers use this public key to verify that the email hasn’t been altered and is truly from your domain.
DMARC (Domain-based Message Authentication, Reporting & Conformance)
Finally, set up a DMARC record that tells receiving servers how to handle emails that fail SPF or DKIM checks. Start with a “p=none” policy to monitor authentication results without blocking mail. Over time, move toward stricter policies — “quarantine” or “reject” — once you are confident all legitimate senders are properly authenticated.
Because misconfigurations can lead to legitimate emails being flagged or rejected, many organizations rely on tools to simplify the process. EasyDMARC’s DMARC Record Generator can help you create a valid DMARC record quickly, while the DMARC Record Checker verifies if your setup is working correctly. Together, these tools make implementation faster, more accurate, and aligned with best practices.

Email Authentication Best Practices
Setting up SPF, DKIM, and DMARC is only the first step. To ensure your email authentication framework stays effective, organizations should follow a set of best practices that keep systems secure and aligned with evolving threats.
Publish and Maintain Accurate Records
Make sure your SPF and DKIM records are correctly configured and regularly updated. Outdated or incomplete records can cause legitimate messages to fail authentication.
Start with Monitoring Before Enforcement
When deploying DMARC, begin with a “p=none” policy to collect reports without impacting mail flow. This allows you to identify unauthorized senders and fix issues before moving toward stricter enforcement (quarantine or reject).
Aim for Full DMARC Alignment
DMARC only works effectively when SPF and DKIM are aligned with the visible “From:” address. Ensure that your sending sources are properly authenticated and aligned to prevent failures.
Leverage Reporting and Monitoring Tools
Use DMARC reports to understand who is sending on behalf of your domain. Monitoring these reports helps you detect abuse, spot misconfigurations, and make informed adjustments to your policies.
Work Toward a Reject Policy
The ultimate goal of DMARC is to stop malicious messages completely. Progressively move from monitoring to “quarantine” and eventually to “reject” once your legitimate sources are fully authenticated.
Consider Advanced Protections
Once your domain is DMARC-compliant, you can enable standards like BIMI to display your brand logo in inboxes. This adds another layer of trust and visibility to your messages.
Automate Where Possible
Managing multiple DNS records manually can become complex. Solutions like EasyDMARC’s platform simplify record generation, monitoring, and enforcement, reducing human error and saving time.
Email Authentication as a Service
Email authentication as a service gives businesses a streamlined way to secure their email systems without taking on the technical burden in-house. Instead of managing complex protocols alone, organizations can rely on EasyDMARC’s Managed Services team to handle the entire process from setup to ongoing monitoring.
With this approach, companies benefit from:
- Expert guidance: A dedicated DMARC Engineer and Customer Success Manager provide step-by-step support via video calls, 24/7 email correspondence, and quarterly domain security reviews.
- Comprehensive setup: Our team repairs, establishes, and maintains SPF and DKIM records, while configuring DMARC policies to gradually reach enforcement (p=reject).
- Continuous monitoring: EasyDMARC experts track DMARC reports, flag unauthorized senders, and take action to maintain a secure email ecosystem.
- Improved deliverability and reputation: Proper authentication ensures messages land in inboxes, builds sender credibility, and reduces the risk of phishing and spoofing.
- Peace of mind: Businesses stay aligned with industry best practices, knowing their authentication is always current and effective.
This service ensures that email authentication is not only implemented correctly but also maintained over time, giving organizations confidence and protection in all communications.
Final Thoughts
Email authentication has become an essential layer of defense against today’s evolving cyber threats. Without it, organizations leave their domains open to phishing, spoofing, and impersonation attacks that can damage customer trust and harm brand reputation. By implementing SPF, DKIM, and DMARC together, businesses ensure their emails are verified at every step of the journey — improving deliverability, protecting their brand, and maintaining secure communication with partners and customers.
Getting email authentication right, however, can be challenging. Records must be configured correctly, policies aligned, and enforcement levels adjusted carefully to avoid blocking legitimate messages. This is where EasyDMARC makes the process simpler. Our platform is built to help organizations of all sizes deploy, monitor, and manage email authentication with ease.
Email authentication is a critical component of every organization’s security strategy. With the right protocols and tools in place, you can safeguard your communications, build trust with your audience, and stay ahead of cybercriminals.
If you haven’t implemented DMARC, now’s the time to start. Feel free to reach out today!
Frequently Asked Questions
Effectiveness can be measured by monitoring DMARC reports to track how many emails pass SPF, DKIM, and DMARC checks. A reduction in spoofed or unauthorized emails, improved deliverability, and higher inbox placement rates are strong indicators that authentication protocols are working as intended.
Platforms like EasyDMARC provide record generators, checkers, and analyzers that make managing SPF, DKIM, and DMARC records straightforward. These tools simplify record creation and validation without requiring deep technical knowledge.
By using automated tools or managed services, businesses can offload the manual effort of configuring and maintaining records. Features like guided wizards, automated policy updates, and continuous monitoring reduce time spent troubleshooting or editing DNS entries.
Organizations should look for solutions that offer:
– Easy record generation and validation
– Scalable monitoring and reporting
– Automated alignment checks
– Support for BIMI and advanced security features
– Reliable customer support and guidance
These factors ensure the platform meets both current needs and future growth.
SaaS providers should implement SPF, DKIM, and DMARC across all sending domains, starting with monitoring mode and gradually moving to enforcement. They should also centralize reporting, ensure third-party senders (like CRMs or email marketing tools) are properly authenticated, and use BIMI to build trust and brand visibility in client inboxes.
Email authentication services protect your brand by preventing attackers from spoofing your domain in phishing campaigns. Strong DMARC enforcement blocks fraudulent messages before they reach recipients, while BIMI adds visual brand recognition in inboxes. This combination builds customer trust and protects brand reputation.





