How To Spot Phishing Emails
Phishing is a hacker-favorite method of stealing personal information. While there are a few other ways to deliver malicious links (voice messages or SMS), phishing email is the most common one for organizations.
As promised in the previous module 2, here we give you tips and tactics to spot and avoid falling prey to phishing emails.
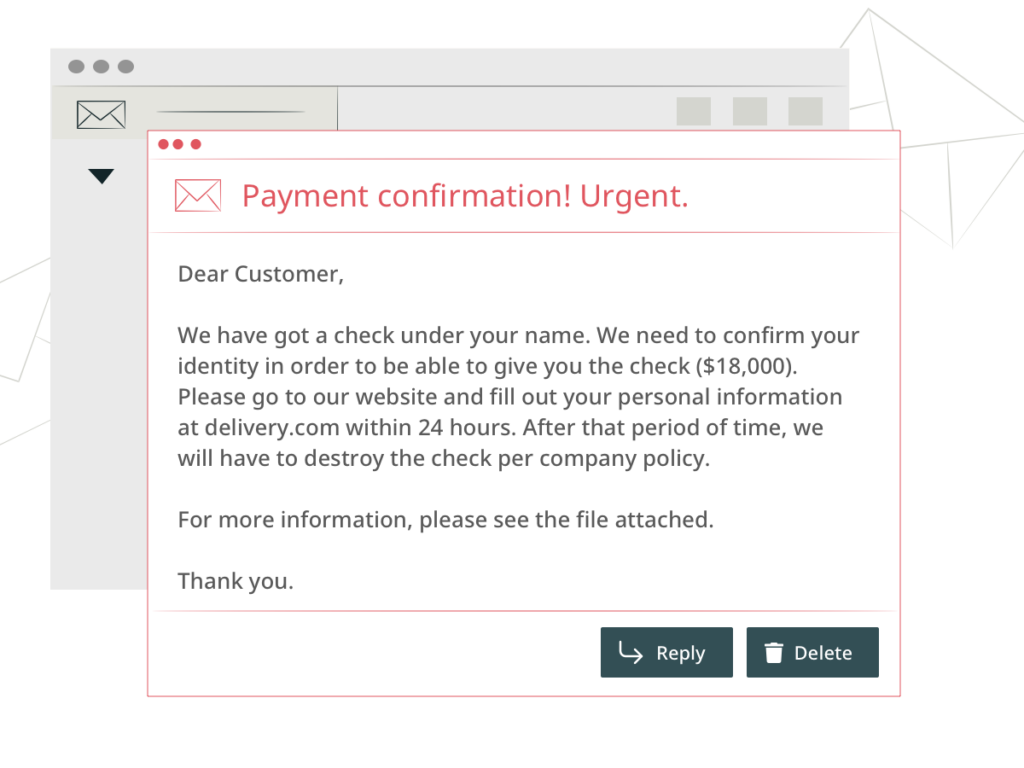
Let’s start with a sample. The picture below will show you most of the indicators of a phishing campaign. We also describe them in detail further in the article.
Emails With Generic Greeting or Email Text
Most companies personalize their emails to customers. So do the partners and colleagues. Phishing emails usually contain a generic greeting like “Dear customer” or “Dear colleague.” Although this is more common with mass phishing attacks, spear attackers might also make the mistake of not addressing you by name. In addition to this, you should look for general text patterns throughout the message.
Emails With Grammar and Spelling Mistakes
Many companies use spell-checking tools, have copy editors, and ensure their emails have top grammar and spelling quality. Even if the company isn’t located in a native-speaking country, the messages get checked before clicking the “Send” button.
Most hackers don’t think about looking good, keeping a company reputation, or aren’t native to the language they’re using. So, they don’t spend too many resources on message craftsmanship in a phishing email.
Messages With Inconsistencies in the Return Address
Cyber threat actors usually open similar websites and deceptive email addresses that look almost like the real person or company. We recommend that you verify the domain name first, then you might want to search for the sender in your inbox. Minor inconsistencies like a dot or underscore in the name, a typo, or a weird-looking top-level domain should trigger mistrust.
Suspicious Attachments
Don’t open suspicious attachments, especially those commonly associated with malware (.zip, .exe, .scr, etc.). Always run diagnostics on the files you download, using a trustworthy antivirus program.
Too Good to Be True
The general rule of thumb is that it’s most probably a scam if you receive help or heritage over email. Incentivizing unsuspecting recipients with a possible reward is the hackers’ specialty. During intricately crafted spear-phishing campaigns, the attacker might know your name, but it’s usually a phishing attempt if the offer is too tempting.
Emails With False Sense of Urgency
Many phishing emails include an urgency in the email message to rush the recipients to take action without studying the email properly. Don’t fall for it. Find the company’s contact number and call them for clarification.
Emails With Only One Contact
Most companies offer at least an email, a phone number, and live chat, i. e., more than one way to contact them for support. If the email doesn’t give you alternate means of communication, flag it as suspicious. You should also check the company’s website to ensure it isn’t fake.
Conclusion
Although spotting phishing emails and dealing with them is a reactive tactic against cyberthreats, it’s not the worst. However, leaving it to chance can wreck havoc to your organization. The next module dwells on two case studies, showing what happens to large organizations when they neglect email security.