A DMARC fail is when an email sent from a domain fails to pass authentication checks, leading to potential rejection or quarantining. Understanding why DMARC fails is essential to safeguarding your domain from phishing and spoofing threats and ensuring high email deliverability rates. DMARC authentication, an email security protocol, works with SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to verify the legitimacy of emails sent from your domain.
Key causes for DMARC (Domain-based Message Authentication, Reporting & Conformance) failure include:
- Emails landing in spam folders instead of inboxes
- Complete rejection of messages by receiving mail servers
- Delivery delays affecting time-sensitive communications
- Damage to your domain’s sending reputation
- Potential security alerts for your recipients
When you encounter a DMARC error, it signals that something in your email authentication chain isn’t working properly. This authentication problem can significantly impact your email deliverability and business communications.
What Causes DMARC to Fail?
- Misconfigured DKIM signatures – Your digital signatures may contain errors in the DNS records or cryptographic keys, preventing proper verification of your email’s authenticity
- Third-party provider misalignments – Services sending emails on your behalf (like marketing platforms or CRMs) may not be properly authorized in your DMARC policy, causing authentication failures
- Email forwarding issues – When messages are forwarded, the original authentication data can be altered or lost, triggering DMARC failures even for legitimate communications
- Domain spoofing – Malicious actors may be attempting to impersonate your domain, which DMARC correctly identifies and blocks, though this can be confused with legitimate mail failures
This blog will explore DMARC authentication failures. We’ll start by defining what DMARC failure means and how it affects email delivery. Then we’ll examine common causes behind these failures, including configuration errors, third-party sending issues, and implementation mistakes. Finally, we’ll provide practical solutions to fix DMARC problems, offering troubleshooting steps and best practices to improve your email deliverability and strengthen security.
What does DMARC Failure Mean?
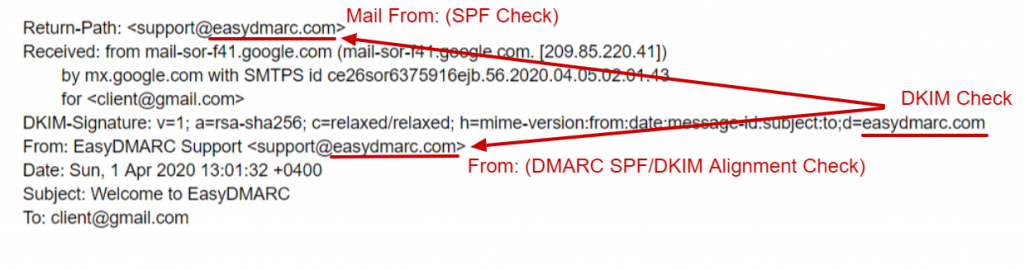
DMARC failure occurs when an email sent from your domain does not pass the DMARC authentication check, which relies on both SPF and DKIM authentication and domain alignment between SPF, DKIM, and the email’s “From” address. Domain alignment, the core concept of DMARC, verifies that the email address in the “From” email header matches the actual sender. This alignment requires that both the domain in the SPF check (based on the Envelope From or Return-Path address) and the DKIM signing domain (represented as d=example.net) match the domain shown in the “From” address.
When either SPF or DKIM is misaligned with the “From” domain, DMARC will fail, indicating that the email could be unauthorized or fraudulent. Proper SPF and DKIM alignment is essential to secure your domain and prevent misuse.
Causes of Failure
1. DKIM Signature Not Set Up
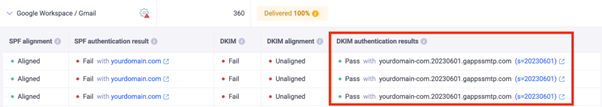
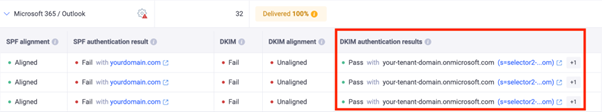
If you don’t configure a custom DKIM signature, email providers like Google and Microsoft will automatically sign your outgoing emails with their default DKIM key (e.g., d=domain.gappssmtp.com for Google). These default signatures don’t represent your domain; instead, they reflect the email provider’s domain. To set up DKIM under your domain, you need to configure the correct DKIM entries in your DNS provider such as GoDaddy, Rackspace, or Cloudflare.
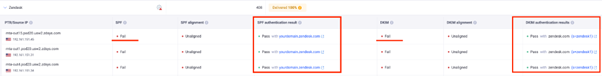
In this case, DMARC fails because of email domain misalignment. If someone receives an email from example.com but it’s signed as example.gappssmtp.com or example.onmicrosoft.com, DMARC won’t recognize it as authorized. You can view examples of this issue, along with screenshots, in the EasyDMARC dashboard.
A DMARC fail due to Google Workspace using the default DKIM Signature, and not authorized in the SPF Record
A DMARC fail due to Microsoft 365 using the default DKIM Signature, and not authorized in the SPF Record
Here’s how you can set up SPF, DKIM, and DMARC for Google Workspace and Microsoft 365 mail.
2. Not Activating Protocols for Third-Party Providers
If you use third-party service providers like MailChimp, SendGrid, HubSpot, and ZenDesk for your marketing, transactional, and help desk emails, you have to permit them to send emails on your domain’s behalf.
That is achieved by pointing DNS entries from your DNS Provider (like GoDaddy, Cloudflare, or Rackspace) to authorize and ‘whitelist’ the given servers.
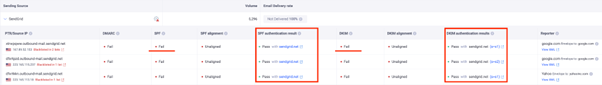
These providers sign your emails with their domain name by default, and your recipients generally see “via sendgrid.net”, “via thirdpartyprovider.com” messages on your emails, thus leading to DMARC misalignment and DMARC failure.
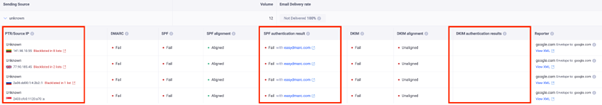
Below, you can see examples of this case with screenshots from the EasyDMARC dashboard.
A DMARC fail due to emails sent through a SendGrid account not properly signed with DKIM and SPF for a unique domain.
A DMARC fail due to emails sent through a ZenDesk account not properly signed with DKIM and SPF for a unique domain.
3. Email Forwarding Has Changed the Original Message
Forwarded emails can often trigger DMARC failures due to the way they are processed by intermediary servers. When an email is forwarded, it may pass through one or more intermediate servers before reaching its final destination. These intermediary servers often have IP addresses that differ from the original sender’s, which can lead to SPF check failures, as the new IP addresses aren’t typically included in the original sender’s SPF record. Although DKIM is generally unaffected by forwarding, modifications by intermediary servers – such as adding or changing message footers – can sometimes disrupt the DKIM signature.
Read more about SPF/DKIM/DMARC behavior during forwarding in this article.
4. Your Domain Has Been Spoofed
If you are a victim of spoofing, cybercriminals are sending emails that appear to come from your domain. Why does DMARC fail in this case? These unauthorized sources don’t pass SPF and DKIM authentication checks, which results in DMARC failure. These failed attempts are categorized under the ‘Threat/Unknown’ tab in your EasyDMARC Dashboard.
DMARC Fails
Here are some general guidelines for fixing DMARC fails.
Ensure SPF Alignment
- Check that your SPF record includes all legitimate sending sources for your domain. If you’re using third-party email services (like marketing platforms or web hosts), ensure their sending IP addresses are included in your SPF record.
- Ensure that the Envelope From or Return-Path address used during email delivery matches your domain or the domains you’ve authorized in your SPF record.
Configure DKIM Properly
- Set up a DKIM digital signature for your domain to sign outgoing emails. If you use third-party email services, ensure they sign emails with your domain’s DKIM key (not their default).
- Check that the d= value in the DKIM signature matches your domain.
- You can use a DKIM checker to be 100% sure your DKIM signature is properly set up.
Check Your Domain Alignment
- For DMARC to pass, the domain in the From email header must match the domain used in the SPF and DKIM checks. If you’re using an email service provider or forwarding service, ensure their systems support proper alignment and don’t modify the message in a way that causes misalignment.
Review Your DMARC Policy
- Ensure your DMARC policy is correctly configured in your DNS settings with a free DMARC checker. You can also start with a p=none policy for monitoring over the first few weeks. Focus on detecting legitimate sources and authenticating them with SPF and DKIM, and then gradually shift to p=quarantine or p=reject as you resolve issues. Closely examine your DMARC reports to identify misalignments or authentication failures.
Monitor Your DMARC Reports
- Use DMARC aggregate reports and forensic or failure reports to track which emails are failing DMARC checks. These reports will help you identify which IPs or services are causing SPF or DKIM issues.
- DMARC reports are usually presented in a complicated XML format. However, EasyDMARC’s platform transforms these reports into user-friendly data. Our algorithm categorizes the reports into “Compliant,” “Non-Compliant,” “Threat/Unknown,” and “Forwarded.” This categorization helps you focus on critical aspects of your email authentication metrics and address any issues.
Consult with Your Email Service Providers
- If third-party services are involved, work with them to ensure proper configuration of your SPF, DKIM, and DMARC records.
You can find more about DMARC in our blog on DMARC RFC.
In Closing
Understanding DMARC failures is part of protecting your domain from phishing and spoofing attacks and aligns with global best practices demonstrated by DMARC adoption in Australia. Proper SPF and DKIM configuration, along with domain alignment, are essential to pass DMARC setup and checks. Common causes of failure include misconfigured DKIM signatures, third-party service misalignments, email forwarding issues, and domain spoofing. By aligning your domain correctly, monitoring DMARC reports, and ensuring proper configuration, you can minimize these failures and enhance your email security. Tools like EasyDMARC can help streamline the process and resolve issues efficiently.