DMARC alignment refers to the relationship between the domains in an email’s “From” header domain and the domains in the email’s authentication results. It builds upon existing email authentication protocols – SPF and DKIM – by introducing critical alignment checks that verify the authenticity of the email sender’s domain and add an extra layer of protection against phishing attacks and email spoofing.
This blog will delve into what DMARC alignment is, how it improves SPF and DKIM protocols, and how to achieve it effectively.
Understanding DMARC Alignment
DMARC alignment focuses on the relationship between the “From:” address in the email header and the domains used in SPF (“Return-Path”) and DKIM (“d=”) checks. Before diving deeper into DMARC (Domain-based Message Authentication, Reporting, and Conformance) alignment, it’s important to understand how the base protocols work:
- SPF (Sender Policy Framework) verifies if the IP address used to send the email is authorized to do so on behalf of the domain. However, SPF only checks the Return-Path address, not the visible From: address.
- DKIM (DomainKeys Identified Mail) adds a digital signature to the email, confirming to email receivers that it hasn’t been altered during transit. While DKIM ensures email integrity, it doesn’t verify which domain actually signed the email.
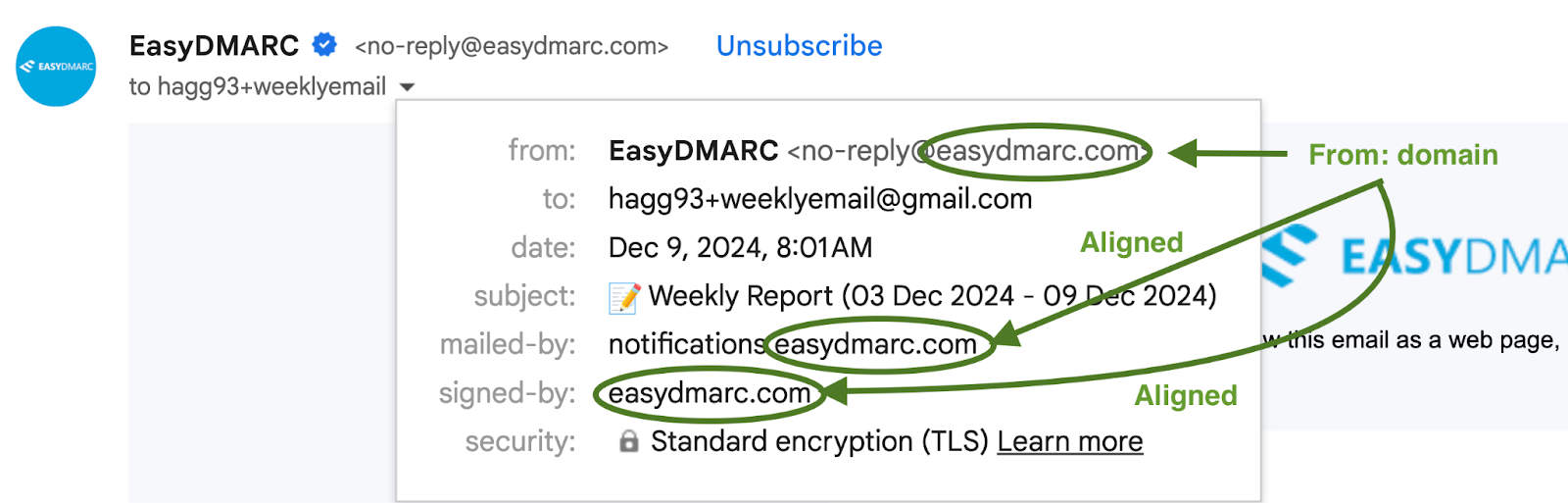
DMARC builds on SPF and DKIM by introducing alignment checks. DMARC alignment ensures that the visible “From:” address in an email message matches the domains authenticated by SPF and DKIM. This is crucial because SPF and DKIM alone do not protect the “From:” address, leaving room for attackers to spoof emails that appear legitimate to end-users. Alignment verifies that the email’s sender is authorized, enhancing domain protection, email security, and email deliverability.
Achieving Alignment with Email Service Providers
The process for achieving DMARC alignment with Email Service Providers (ESPs) varies depending on the provider’s requirements and SPF and DKIM record configuration methods. Here’s a general guide:
Overall Approach
- Configure SPF and DKIM records provided by your ESP in your DNS portal. This allows you to authenticate emails sent from your domain and improve deliverability.
Configuration by ESP Type
- For major providers such as Google Workspace and Microsoft 365:
- SPF Records: Use the “include:” mechanism to include the ESP’s IP addresses in your domain’s SPF record.
- DKIM Records: Implement the DKIM record (TXT or CNAME record) exactly to ensure email signatures align with your domain.
- For bulk sending ESPs such as SendGrid, MailGun, and MailChimp:
- SPF Records: Often configured using CNAME records at a subdomain level. Some ESPs may only provide DKIM records and not support SPF alignment.
- DKIM Records: Typically provided as CNAME records.
- Note: Some ESPs also require TXT verification and MX records for bounce handling.
EasyDMARC makes the process of DMARC alignment much simpler, with over 1,400 identified email sources visible in our DMARC aggregate reports. Customers can also get detailed instructions on adding SPF and DKIM records specific to their ESP.
Strict vs. Relaxed Alignment
DMARC alignment can be strict or relaxed, which is determined by the settings for your SPF alignment (aspf) and DKIM alignment (adkim). These settings dictate how strictly your domain aligns with authentication mechanisms like SPF and DKIM.
By default, DMARC uses relaxed alignment (denoted by “r”). This is generally recommended, especially for domains with multiple subdomains (e.g. marketing.example.com, support.example.com). With relaxed mode, the “From” address and the domain used in the SPF/DKIM check can belong to the same organization, even if they have different subdomains.
Strict alignment mode (denoted by “s”) requires an exact match between all domains. While offering an extra security layer, it can inadvertently block legitimate emails from subdomains.
Relaxed Alignment
- aspf=r: The email domain in the Return-Path (SPF record check) only needs to match the organizational domain of the “From” address. For example, emails from mail.example.com align with example.com.
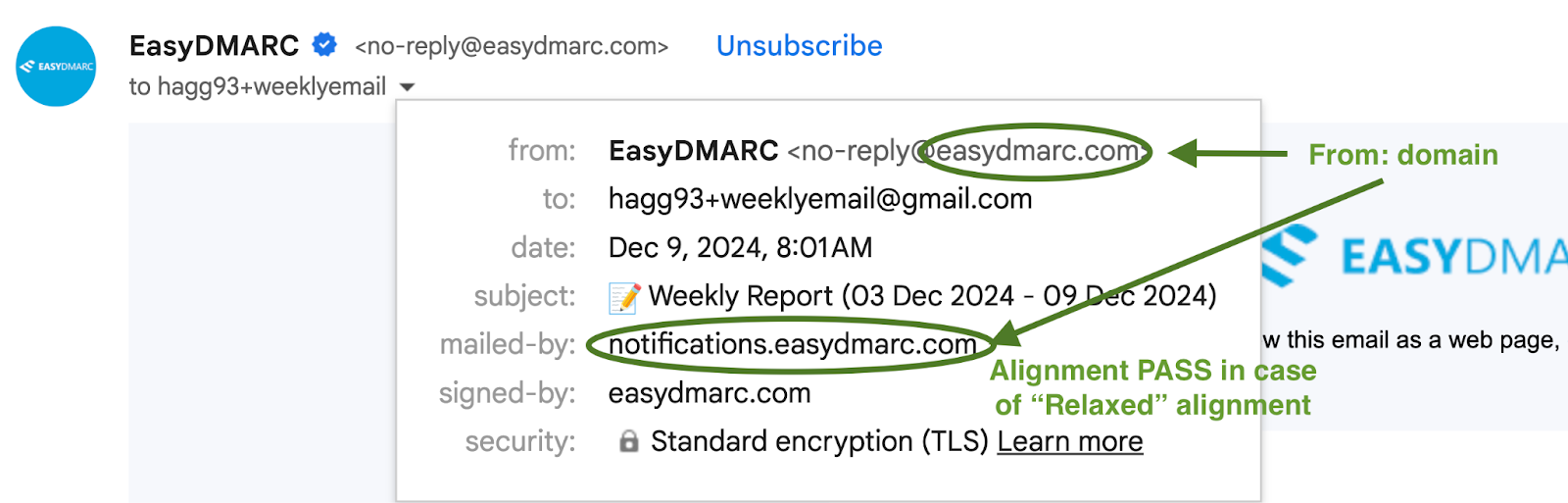
- adkim=r: The signing domain in the DKIM signature (d=) must belong to the same organization as the “From” address. Subdomains are permitted.
Strict Alignment
- aspf=s: The Return-Path domain must exactly match the “From” domain. Emails from mail.example.com fail alignment if the “From” domain is example.com.
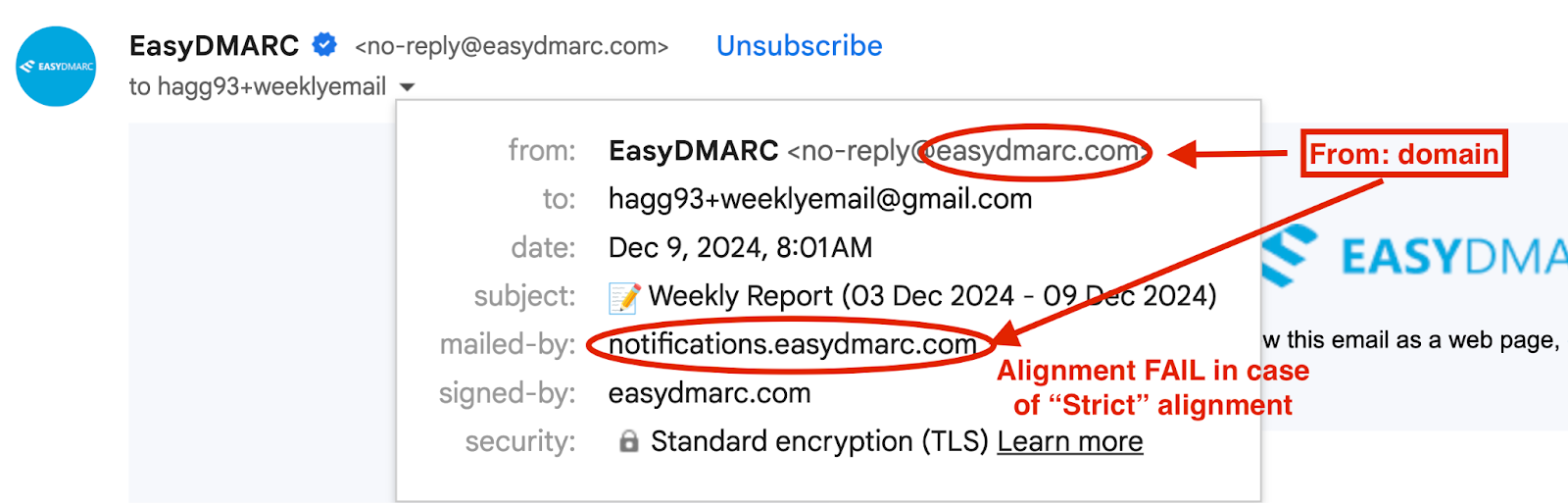
- adkim=s: The DKIM signature domain must exactly match the “From” domain, with no allowances for subdomains.
For domains using subdomains or third-party email services, relaxed alignment ensures smoother operations without compromising authentication. Strict mode, while more secure, is ideal for simpler domain setups where exact matches are achievable. Balancing these settings depends on your security needs and the complexity of your email infrastructure. If your DMARC policy is set at p=reject, mail servers will block suspicious emails even with relaxed alignment.
Best Practices for DMARC Alignment
When implementing DMARC alignment, follow these recommendations:
- Relaxed Mode is Recommended
If you use third-party email services and subdomains, then you should keep relaxed alignment mode. Remember, when it comes to achieving robust email security with DMARC, it is your DMARC policy that matters most. A p=reject policy ensures all illegitimate email flows are blocked.
2. ESP Configuration
Carefully follow your ESP’s specific instructions for DNS record setup:
- Add all recommended ‘include’ mechanisms for SPF
- Implement CNAME records as specified
- Ensure proper DKIM key rotation and management
3. Monitor DMARC Reports
Utilize both aggregate and failure reports to track authentication outcomes and identify potential issues:
- Aggregate Reports provide an overview of email authentication outcomes
- Failure Reports offer detailed insights into individual authentication failures
If you are an EasyDMARC customer, achieving these best practices is streamlined with our EasyDMARC platform.
The DMARC Framework
The benefits of DMARC, of course, go beyond alignment, offering a comprehensive framework for email security:
- Authentication: Ensures emails are legitimate by combining SPF, DKIM, and alignment checks.
- Reporting: Provides two types of reports for monitoring and managing email authentication:
- Aggregate Reports: Summarize email authentication outcomes, including email delivery status, IP addresses, and SPF/DKIM results.
- Failure Reports: Offer detailed insights into individual emails that fail DMARC checks (limited support due to privacy concerns).
- Conformance: Allows domain owners to define a DMARC policy (p=none, p=quarantine, or p=reject) for handling emails that fail DMARC checks.
Conclusion
DMARC alignment is a crucial component of email security, bridging gaps left by SPF and DKIM protocols alone. By ensuring that both protocols align with the visible “From:” address, organizations can protect their domains from spoofing attacks while ensuring legitimate emails reach their recipients.
With EasyDMARC, achieving DMARC alignment becomes a straightforward process, ensuring your domain is secure, and your emails are trusted. By enforcing alignment and leveraging detailed reporting with DMARC checker, organizations can strengthen their defenses against phishing and spoofing attacks. Contact us today to find out how we can help you.





