Educational institutions are attractive to malicious actors for various reasons, including the abundance of personally identifiable information (PII), infrastructure, and finances. That’s why security incidents are common in universities.
From large universities to small community colleges, educational institutions are all potential targets for malicious cyber attacks, leading to financial loss and sensitive data leaks. This article digs into some of the most significant security breaches in the education sector in recent years. It also discusses how organizations can protect themselves from similar incidents in the future.
Northwestern Polytechnical University Phishing Attempts
In June 2022, hackers from abroad were caught sending phishing emails containing Trojans to teachers and students at Northwestern Polytechnical University in Northwest China’s Shaanxi Province, attempting to steal their data and personal information.
The university kept the phishing attempt and data leakage at bay and avoided losses due to its improved security capabilities.
The university officials say they’ve been paying great attention to cybersecurity and digital hygiene, with regular inspections and increased sensitivity among teachers and students.
Contrary to what you might expect, Northwestern Polytechnical University still misses a DKIM record at the time of writing, and its DMARC policy is still on p=none.
The New Mexico School District Ransomware Attack
In February 2020, the Gadsden Independent School District was hit by the same ransomware for the second time in the same year.
The district announced that its internet and communications systems, including phone service, were down in 24 schools. Student data and personnel records were reportedly unaffected.
This most recent ransomware attack was attributed to the Ryuk virus, which was also responsible for disabling the district’s email systems in July 2019.
After the previous attack, the district’s technology department worked hard to remedy the harm done by the malware.
The attack against Gadsden ISD is just one of 24 known ransomware attacks on school districts in the U.S. since August 2019.
It’s unclear if the attack started from an email, but it has affected servers, computers, and other infrastructure components. The school district’s IT staff had to rebuild their email environment from scratch, showing how crucial it is to shield the “transit communication system.”
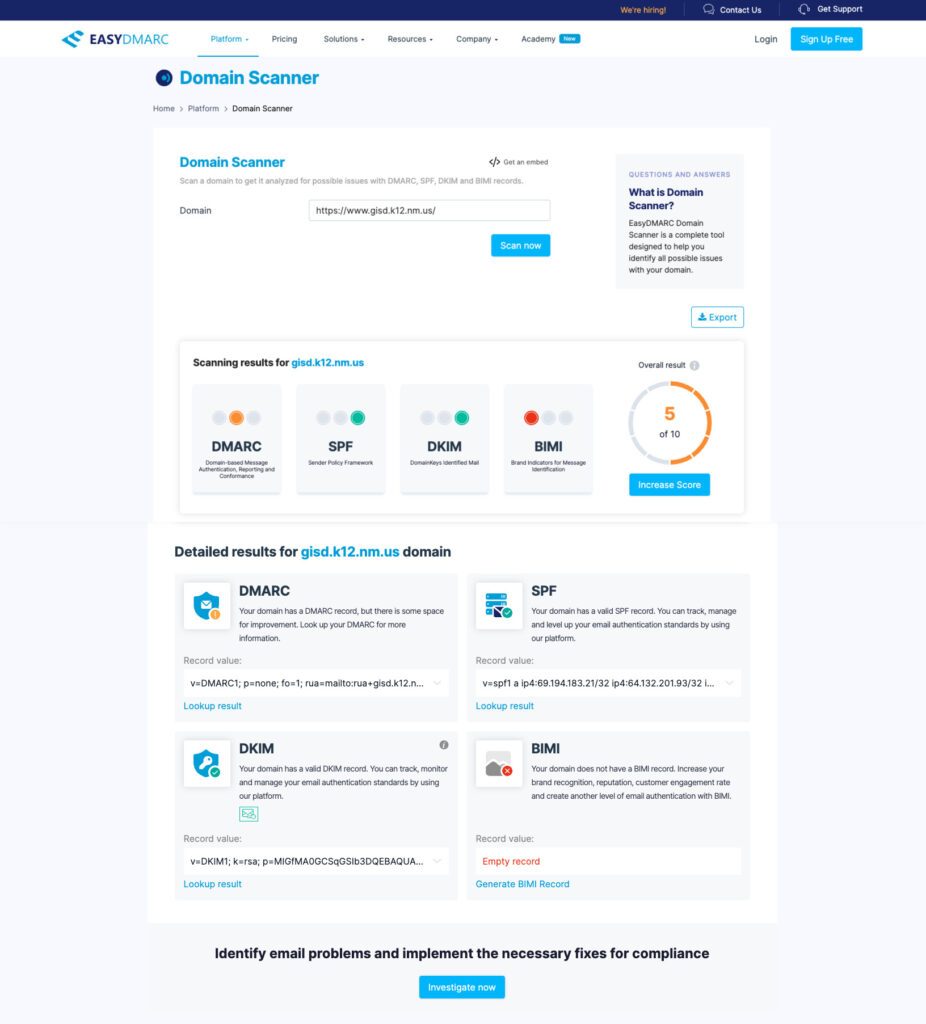
We’ve decided to check how good of a job they’ve done since, so we fired up our domain tester and checked Gadsden Independent School District’s website.
They’ve done a great job establishing two email authentication protocols: SPF and DKIM. However, their DMARC record has some room for improvement.
Fully implement the three-step email authentication process to provide unwavering security to any domain infrastructure.
While Gadsden Independent School District does have a valid DMARC record, they still don’t enjoy full protection against email-borne cyberattacks, including ransomware. Their DMARC record is in p=none, meaning it only monitors email senders and doesn’t block malicious ones. This means they still need to enforce the DMARC policy to its highest security mode.
If you’re interested in ransomware protection, here are some helpful articles to get you started:
University of Deakin Data Breach
In 2022 Deakin University revealed a data breach impacting almost 47,000 current and past students, along with a smishing attack that compromised a legitimate communications channel and targeted 10,000 current students.
The Victorian university said it experienced the data breach since a single staff member’s login credentials were compromised. One small win, like access to a key account, allowed the attacker to access a third-party provider that sends messages to students via SMS. Hackers then launched a smishing attack affecting 10,000 Deakin students, the university said.
The smish was a parcel delivery scam that directed students to a web form that sought additional information (in this case, a payment card) to free the delivery from customs.
The attacker could also have downloaded the personal and contact details of 46,980 Deakin students and alums.
Deakin University said it would report the breach and seek guidance from the Office of the Victorian Information Commissioner (OVIC).
In this case, one error on the educational institution’s side endangered tens of thousands of people. While there are convenient tools for checking phishing URLs, some victims were bound to follow the bait – it’s just how the human factor works in cybersecurity.
We’ve got some tips for data breach prevention in the articles below:
Conclusion
The education industry is particularly vulnerable to security breaches due to its sensitive data and information. To protect themselves from similar incidents in the future, organizations should implement measures such as patching and updating their software, using firewalls and intrusion detection systems, monitoring for suspicious activity, and having a data breach response plan in place.
While it’s essential to take emergency actions after a security breach or attack, you should always think ahead. Protecting your domain infrastructure is just one of the security must-haves, but but having a strong partner beside you can be the difference between a bumpy road and smooth sailing.
Sign up with EasyDMARC to start your journey to DMARC compliance.









