What is SMTP?
In 1982, when researchers discovered the simplest mail transfer protocol, they couldn’t anticipate that email phishing would become a global issue for a lot of companies and users, but in time, the number of spam emails started to grow increasingly.
Simple Mail Transfer Protocol or SMTP is designed as a mail transmission system that allows you to deliver your message to another person. This simple protocol is responsible for emails transmission. MTA (mail transfer agent) and MUA (mail user agent) are sender and the recipient servers. This simple protocol helps you send and receive emails. MUA is an email client. It allows users to read your messages.
We’re buried in various email delivery programs, both web-based and downloadable, as well as desktop and mobile. For example, Microsoft Outlook and Eudora store your emails on your computer. Others, such as Yahoo and Hotmail, store and collect your emails on their mail server. The beauty of SMTP is that the mentioned programs all leverage it for sending and receiving emails.
However, SMTP also has weaknesses, one of them being the fact that all emails are simple TXT messages, which are extremely easy to compromise.
According to a recent IBM research, 78% of all attacks against OT heavy industries start with phishing.
However, all industries are prone to these attacks, so using appropriate email protection solutions is crucial for any business.
What are Email Spoofing and Phishing?
Email phishing is a cyber act of data theft. Phishers can steal your sensitive data, username and password, bank account information, and email address to communicate with your contacts (impersonation attack). The purpose of a phishing attack is to pretend to be a person whom you’re in email communication with under a pretext. So, a phisher is a person who creates spoofed emails.
According to an article in Cybersecurity Dive, phishing cost U. S. companies around $14.8 million per year in 2021.
Here is an example of email phishing.
Hi, Dear Marie,
Hope, everything is fine. Today I made some credit card updates. Here is my account number ***, and please transfer my money to this account today.
Sincerely,David
CEO and Founder of example company.
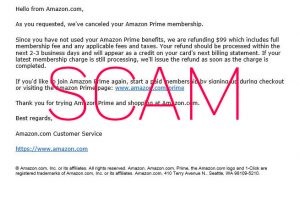
Would you like your accountant to send your money to another phisher guy by deception? Of course not. So, this is an amazing journey for you to understand the DMARC against phishing concept and learn how DMARC implementation can increase your business trust.
What Can You Do to Stop Email Phishing Attacks?
You can build a DMARC record to stop hackers from stealing your private data, communicating on your behalf, or using your personal email address for violation purposes. Plus, DMARC can help you increase your email deliverability and help your emails to reach customers’ inboxes. So, be responsible enough to use DMARC record generator, because business data security is more than important.
If you’re a businessman, a bank officer, a chief marketing specialist or an engineer and you’re worried about your data privacy, accounts information security, then this article is really useful and helpful for you.
“According to the researches, 34.9% of all spear-phishing email was directed at an organization in the financial industry”. You can check urls at Openphish.
Why is Protected Email Important?
In our age, protected email is important, because it helps you connect with your colleagues, friends, or family members at the highest level of security.
There are several benefits of protected or secured emails:
- avoid business risks
- protect confidential information
- nullify message replay possibilities
- avoid identity theft
- repudiate sent messages
Is Phishing a Common Issue?
As stated by Hubspot, 86% of professionals prefer to use email to communicate for business purposes. Other researches show that email is the third most influential source of information for B2B customers. There’s interesting research by Themarketinghelpline that you can check.
The facts and figures we’ve mentioned and countless other research papers emphasize the importance of anti-phishing protection. But facts are nothing if you don’t pay attention to the methods that protect against phishing. Let’s dive into some of the DNS protocols that can guard your domain infrastructure long-term.
SPF and DKIM Protocols
SPF protocol is an address validation mechanism in the DNS record that checks the email address origin. DKIM, on the other hand, uses an encrypted signature to check the sender’s DNS records to verify the email source. SPF and DKIM are very much like matching necklaces with a lock and key or friendship bracelets that become whole once they come together. DKIM is the key that opens the SPF source.
How Does DMARC Prevent Phishing: SPF and DKIM Come Together!
DMARC is an email authentication or validation protocol based on SPF and DKIM. Still, how does DMARC prevent phishing?
DMARC (Domain-based Message Authentication, Reporting Conformance) helps you control sending sources and keep an eye on your domain ecosystem. You can generate and configure your DMARC record with EasyDMARC’s free tools.
If you don’t have a DMARC policy, it’s really easy to setup a spambot that will break your email ecosystem and spoof your domain. While DMARC doesn’t decrease the number of attempts, it just monitors and, depending on your DMARC policy, decides what to do with non-authorized email traffic.
DMARC has three policies:
- p= none: This is the monitoring mode that lets you analyze DMARC reports. However, this policy doesn’t stop spoofed emails from going to the receiver’s inbox.
- p=quarantine: DMARC reports come through for monitoring. However, unauthorized emails go to the junk or spam folders.
- p=reject: This policy is the most strict one. It intercepts spoofed emails and blocks them from reaching the recipient.
Using DMARC against phishing is efficient because it builds upon SPF and DKIM, bringing both into alignment.
Let’s Conclude
If you’re still asking, “How does DMARC prevent phishing?” Here is one takeaway.
In a nutshell, the protocol allows domain owners to place rules in the DNS about how to treat unauthorized sources. As a result, the email infrastructure gains resistance against bad actors that try to leverage any vulnerability in the system. Plus, it lets you control your brand identity, blocking any illegitimate communication attempts. DMARC’s anti-phishing capabilities go beyond protection from spoofed emails. As a byproduct, DMARC and the whole email authentication process help your domain build trust with internet service providers and improve deliverability.





