DMARC (Domain-based Message Authentication, Reporting, and Conformance) is an email authentication protocol that protects business domains from phishing and spoofing. Its main function is to ensure that no threat passes through your domain infrastructure defenses.
DMARC reports, an integral part of implementing DMARC, are the key to achieving full protection. They’re the window into your sender sources and their configuration status, so understanding DMARC reports is crucial. This article explains the types and benefits of DMARC reports, provides examples, and offers step-by-step instructions for analyzing them.
What is a DMARC Report?
DMARC reports contain essential information about the authenticity status of emails sent on behalf of a domain. You start receiving DMARC reports by mentioning an email address (URI) in the “rua” and “ruf” tags of your DMARC record.
The first reports arrive soon after you create a DMARC record and publish it in your Domain Name System (DNS). Learning how to read DMARC reports is crucial for compliance and hardening domain protection.
There are two different types of DMARC reports – Failure (“ruf” tag) and Aggregate (“rua” tag). Each report type serves a different purpose, but more about that later in the article.
Let’s understand why reviewing and acting on DMARC reports is crucial.
How to Read DMARC Reports
DMARC reports are your main working document if you want to reach DMARC compliance. They contain information about your email sending volumes, sources, DMARC policy and alignment settings, and other details.
DMARC reports, including those from DMARC checker, provide a bird’s eye view of your domain infrastructure. By analyzing them, you can detect malicious emails that claim to be from your domain. Without DMARC reports, you wouldn’t be able to know where to start your source configuration journey. They also hint towards the sources to configure and issues to fix.
The DMARC reports you receive on the email address mentioned can be overwhelming, especially when you send bulk emails regularly.
Fortunately, you can easily collect and analyze this information with EasyDMARC’s DMARC report analyzer. Replace your email address with the one provided by our platform specifically for that purpose.
EasyDMARC parses DMARC reports, making them more readable and easy to understand.
How to Enable DMARC Reports: a Step-by-Step Guide
To receive DMARC reports, you need to enable them. You can create and add a DMARC record to your DNS. The process is simple, and it’s the same for all domain providers:
- First, you need to create a DMARC record for your domain. EasyDMARC’s Free DMARC Record Generator tool makes this process quick and easy.
- Enter your chosen email address in the ‘Report Email’ section to receive DMARC aggregate reports during this process.
- Next, enter your preferred email address in the ‘Failure Reporting’ section to receive forensic DMARC reports.
- Input the necessary details and hit the ‘Generate’ button.
- Once ready, publish the record in your DNS zone.
Types of DMARC Reports
There are two main types of DMARC reports: aggregate and failure reports. The email receiver sends these reports, and they serve different purposes.
What is a DMARC Aggregate Report?
DMARC aggregate reports are XML documents that provide information about the authentication status of DMARC, SPF, and DKIM. This data is sent to the “rua” address and contains no sensitive information about email messages.
It encompasses aggregate information, including:
- Reporting ESP information
- Header-from domain
- DMARC policy and alignment settings
- Sender’s IP address
- Message authentication status and data
- Number of messages sent
You can specify the frequency of receiving aggregate reports on the DMARC report under the “ri” tag. The default is 24 hours, but you can change it to any other convenient interval.
EasyDMARC’s user-friendly DMARC Aggregate XML Reports Analyzer makes working with your data and sending sources practical. It also gives you an overview of your email infrastructure.
If you want aggregate reports sent to your EasyDMARC dashboard, use EasyDMARC’s URI for the “rua” tag. Here’s an example of the tag usage in your DMARC record:
v=DMARC1; p=none; rua=mailto:xxxxx@easy-blog;
What is a DMARC Failure Report?
Failure reports go to the “ruf” tag address. They’re simple copies of emails that fail authentication checks. Failure reports provide information that can help identify the true origin of legitimate email sources that need further configuration.
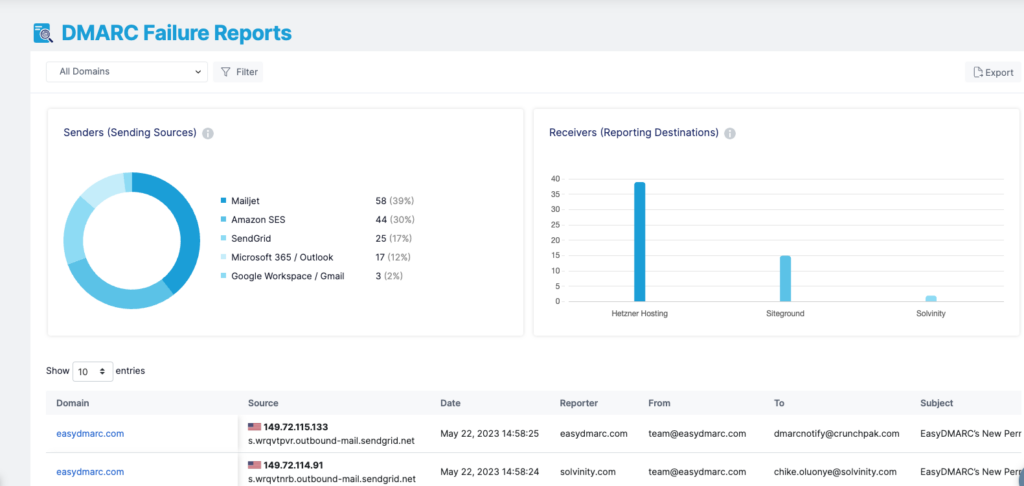
Often, email services don’t provide forensic reports because of privacy concerns. If you’re just starting with DMARC, we recommend you concentrate on monitoring and acting on aggregate reports.
If you want to receive failure reports on your EasyDMARC dashboard, publish a DMARC record and include the “ruf” tag:
v=DMARC1; p=none; rua=mailto:xxxxx@easy-blog; ruf=mailto:rufxxxxx@easy-blog
How to Analyze DMARC Aggregate Reports with EasyDMARC
If you’ve correctly updated your DMARC record with EasyDMARC’s “rua” address, you will start receiving DMARC reports in a complicated XML format. Our system parses these reports into easy-to-read and easy-to-understand data.
Here’s an example of the XML file format:
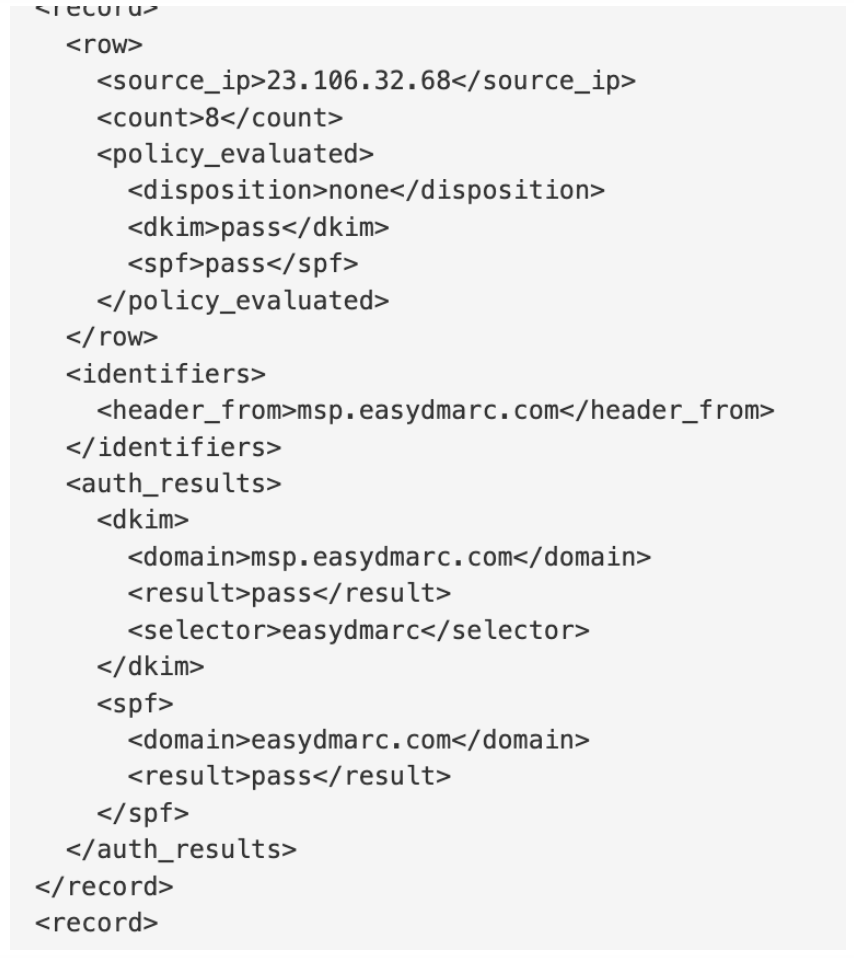
XML files contain essential metrics such as IP addresses, SPF & DKIM health, and the disposition of emails. However, reading multiple reports daily, especially when sending numerous emails, can be challenging.
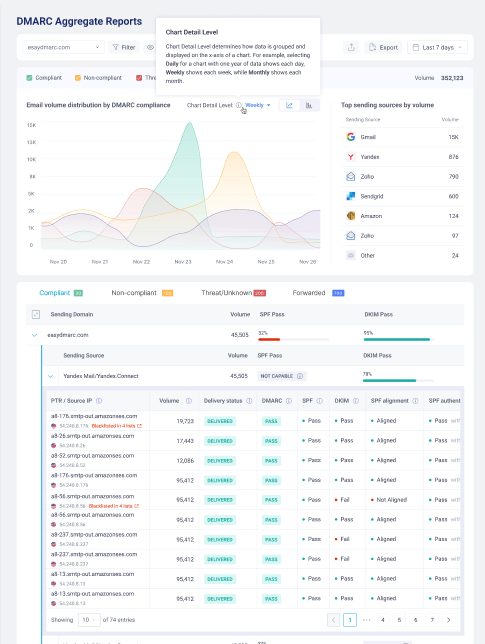
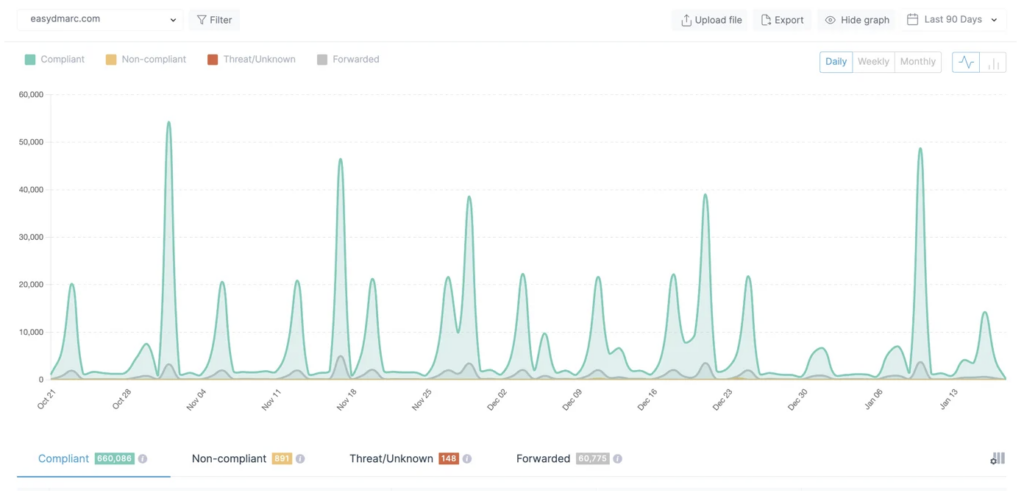
EasyDMARC transforms these reports into user-friendly data, performing additional checks to simplify organizations’ analysis and facilitate appropriate actions. Our algorithm categorizes the reports into four tabs: “Compliant”, “Non-Compliant”, “Threat/Unknown”, and “Forwarded”. These tabs provide centralized reports based on indicators to help you focus on key aspects of your email authentication metrics and address any issues.
Report Details
Let’s examine what sections the report includes and comprehensively understand their significance.
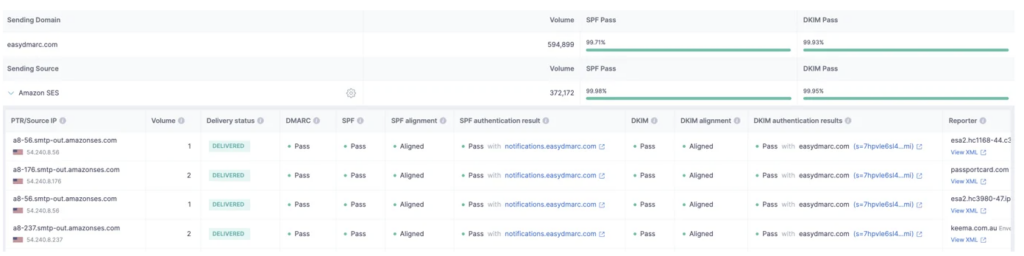
- PTR/IP Source: This is the IP address used by your server to send emails. We identify this IP source to provide you with the service name of your ESP.
- Volume: This indicates the volume of outgoing emails from the given IP address, typically within a 24-hour span.
- Delivery Status: This represents the disposition of your emails, which can be delivered, delivered to spam, or rejected, based on your applied DMARC policy. Under the DMARC Compliant tab, you will see all your delivered emails.
- DMARC: This is the final DMARC result, indicating either pass or fail.
- SPF: This is the final SPF result after checking the SPF Alignment and SPF Authentication results, showing either pass or fail.
- SPF Alignment: This checks if the domain found under SPF Authentication is aligned with the Sending Domain. If it matches, then it’s a pass.
- SPF Authentication: This checks if the Return-Path domain in use is whitelisted in the DNS TXT Record, either your own domain or a third-party domain from your ESP. The result can be pass, fail, neutral, temperror, or permerror.
- DKIM: This is the final DKIM result after checking the DKIM Alignment and DKIM Authentication results, showing either pass or fail.
- DKIM Alignment: This checks if the DKIM Signature domain (d=) used matches the Sending domain.
- DKIM Authentication: This checks if the sent email has a valid DKIM Signature, whether from your own domain or a third-party domain.
- Reporter: This is the ESP that sent us the DMARC reports, essentially your recipients’ servers. They send us the DMARC reports for the emails you’ve sent to them.
- Date: This is the date when your emails were sent for that specific report.
Making DMARC Reports Actionable with EasyDMARC
With every report we receive from major ISPs such as Google, Comcast, and Microsoft, EasyDMARC’s algorithm transforms the data to be human-readable and understandable. It also provides additional information to aid in the action and decision-making process. Understanding DMARC reports is crucial for successfully advancing your DMARC policy to p=reject.
Here are the key points:
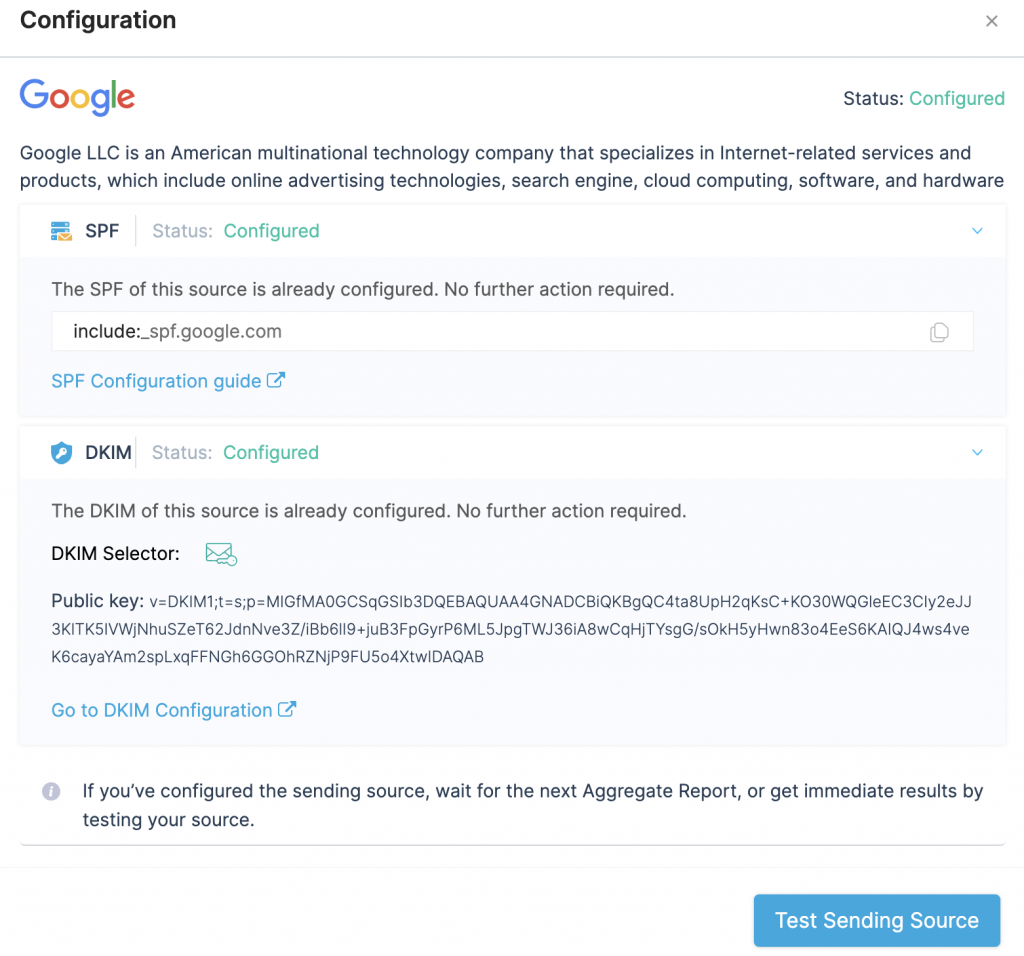
- Email vendor identification: XML files typically contain only the IP addresses used to send emails from your domain. Identifying email sources solely based on IP addresses can be cumbersome and requires manual checks. EasyDMARC simplifies this by performing reverse lookups and providing the source names, so you don’t have to do anything on your end.
- Automated configuration guide: Our engineers have worked extensively to provide detailed configuration guides for specific email sources. This includes official documentation from the source’s website or information from our knowledge base. Ensuring all legitimate sources within your organization are properly configured with SPF and DKIM is a crucial step before moving to DMARC enforcement (p=reject).
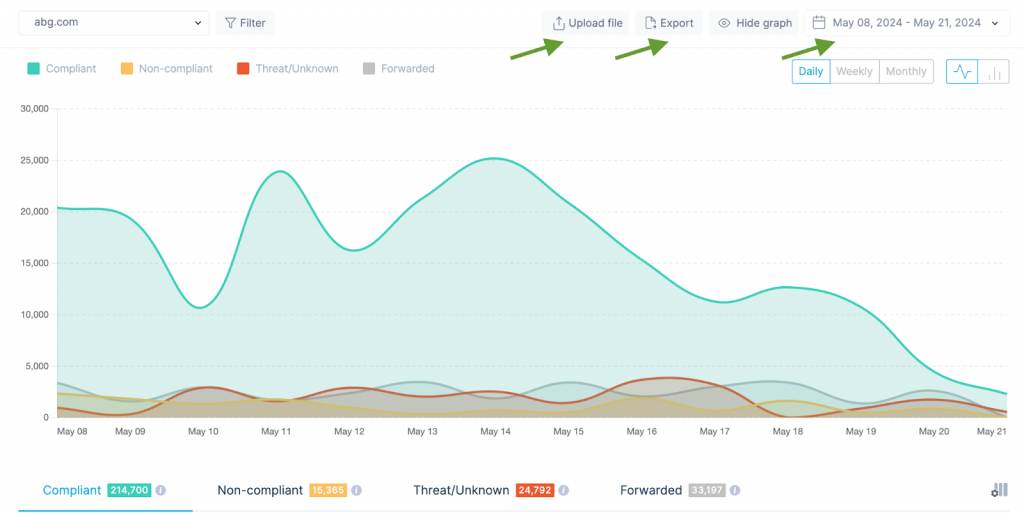
- Filtering: Analyzing reports can be challenging, especially if you send thousands of emails daily using various channels. EasyDMARC offers robust filtering options based on the sender’s details (source name, IP address, SPF/DKIM domains) and the receiver’s details (reporter). This allows you to deeply analyze and address specific situations effectively.
- Additional features: EasyDMARC allows you to upload your own XML files, which is helpful if you’re new to the solution and have existing reports. You can choose any data point to track over custom periods (days, weeks, or months) and export the data for record-keeping or sharing with colleagues.
What to do with DMARC Reports
Here are several recommendations that will help you make the most of DMARC Aggregate reports:
- Always initiate the DMARC implementation with p=none. This will not affect the delivery of Non-Compliant emails. Initial data gathering is crucial to determining the next steps.
- Focus on Non-Compliant sources as they are failing DMARC checks. Identify sources and fix issues by implementing SPF and/or DKIM authentication and alignment. Users can easily follow the steps by clicking on the Gear Icon for each source.
- Identify and fix any SPF or DKIM issues under the Compliant sources. DMARC requires either SPF and/or DKIM to pass, and there might be cases where either of the sources is not configured correctly.
- Monitor data after each fix. Users should ensure that new reports appear under the Compliant tab instead of the Non-Compliant tab, indicating that the source is fixed.
- Verify that every legitimate source used for sending emails is listed under the Compliant tab.
- Ensure that every source under the Compliant tab is DKIM aligned/authenticated. While SPF alignment may not be possible with some ESPs due to limitations, DKIM is usually provided by every ESP.
- After confirmation, users can gradually enforce their policies until p=reject is achieved. Under p=reject, all Non-Compliant and Threat/Unknown reports will fail.
Best Practices for Managing DMARC Reports
DMARC reports are central to DMARC enforcement. Thus, we’ve separated a few best practices to ease you into the process and keep you from making simple mistakes.
Always enable reporting when implementing DMARC : There’s no point in starting DMARC implementation if you don’t receive reports.
Send the reports to a unique address or email group: “rua” and “ruf” tags require an email address or a URI. Still, we don’t recommend using a personal address, as the reports could get lost or mixed up with usual messages.
Analyze your reports to improve DMARC enforcement: Ignoring the reports is bad. However, not following the recommendations they provide is even worse.
Use a dedicated service to interpret DMARC reports: XML files and email sender headers can get overwhelming. A third-party service like EasyDMARC for report analysis can be the light at the end of the tunnel.
Choose EasyDMARC for DMARC Report Analysis
If you send emails, the chances are that you’ve been frustrated by email security and deliverability issues. However, any domain owner who starts their journey with sender policy framework (SPF) and DKIM authentication is on the right track. Add DMARC to the mix and go through the policy enforcement, and you’ll completely safeguard your domain environment.
DMARC reports are vital for the following:
- Monitoring the domain’s email activity
- Viewing authentication results
- Maintaining verified senders
- Identifying fraudsters
However, reading aggregate reports can be challenging because of their format, and failure reports are cumbersome to deal with. At EasyDMARC, we make DMARC reports user-friendly and readable. With our dashboard, you can stop digging for important information and simply act on visualized data.
EasyDMARC offers access to both types of DMARC reporting. You might already receive free DMARC reporting if you’re a free-tier user. You can configure our platform to send more detailed failure or aggregate reports in the Plus tier and above.
Contact our support team if you have questions about our DMARC reporting tools.





