Email-based cybercrimes cost billions of dollars, ranging from $50K per attack for small businesses to $3.86M for mid-size businesses. Phishing emails is one of the common ways of attempting cyberattacks. Hackers use the email domains of reputed companies to trick people into perceiving them as trusted entities. Imagine a malicious actor exploiting your domain and tarnishing your brand image for unethical activities!
Fortunately, DMARC, an email authentication protocol used to prevent unwanted phishing and spoofing can help. EasyDMARC has proven its effectiveness by blocking over 90 million phishing attacks in the first half of 2022.
Statistics like this make it essential to know what DMARC is and the common DMARC tags used. This blog will focus on the same.
What is DMARC and How Does it Work?
Before learning about DMARC tags like fo tag and p tag, let’s see how it works to prevent email-based attacks in your business’ name.
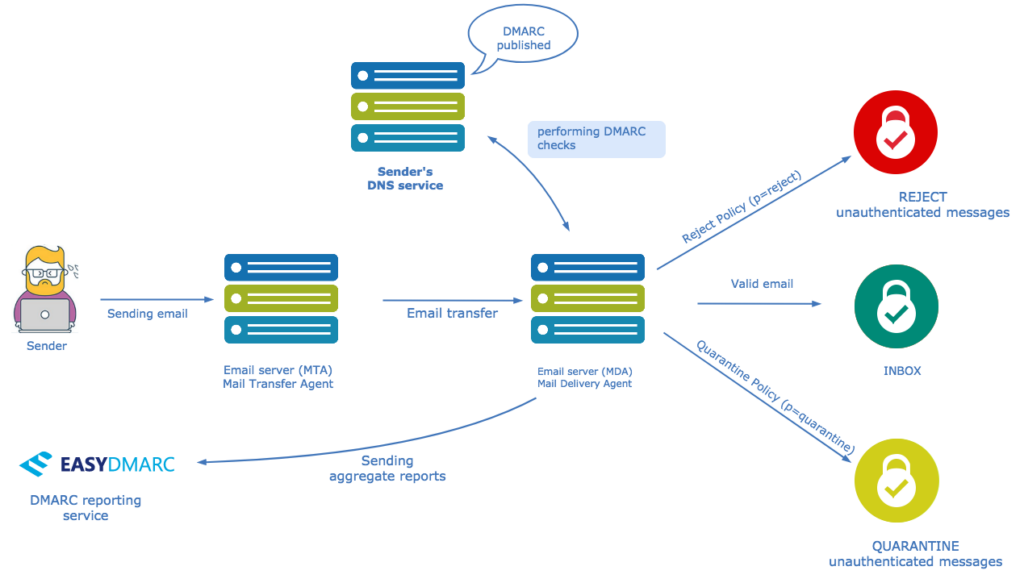
DMARC stands for Domain-based Message Authentication, Reporting, and Conformance. It aligns with SPF and DKIM (other email authentication protocols) and links the sender’s email address and domain name using records published on the DNS.
A legitimate email sometimes fails the SPF or DKIM test. Despite this, mailbox providers allow it to enter if they appear to come from a credible and genuine source. This is because DMARC clarifies the action required in such situations.
DMARC is a DNS TXT record that directs a recipient’s server on dealing with emails from your domain. The server can ‘Quarantine, ‘Reject’, or ‘Allow’ a message as per your DMARC policy.
Where Do You Encounter DMARC Tags?
DMARC tags are used in the DMARC record syntax. A DMARC record is a TXT source record published in DNS. It has a list of DMARC tags, separated by a semi-colon to specify actions a receiving server should take if an email fails the DMARC authentication test.
It has a specified Host/Name; for example, _DMARC.easyDMARC.com is the Host/Name for EasyDMARC. DMARC tag value has tags (like policy or version) and a corresponding value; For example, p=reject. These are paired to direct a recipient’s server on what actions to take.
DMARC Tag Types and What They Do
DMARC tags specify aspects of DMARC implementations and not all of them are as important and as used as the others. They’re divided into three categories.
- Required: These tags are mandatory and you can’t miss them at all. Every DMARC TXT record begins with the mandatory ‘v’ or version tag and the corresponding value of ‘DMARC1’.
- Optional but recommended: It isn’t necessary to add these tags, however they help generate a DMARC report.
- Optional: You can skip these tags completely.
Functions of DMARC Tags
There are total 11 tags that can be applied to a DMARC policy. Of those 11, the “v” and “p” tags are mandatory, and the DMARC rua tag is optional but recommended for receiving the reports. Let’s know what’s the function of each tag.
| DMARC Tag Name | Type | Function |
| v (version) | Required | This DMARC tag tells the version being used. There’s only one version as of now, so it’s always v=DMARC1. |
| p (policy) | Required | The DMARC p tag addresses the DMARC policy mode. It directs the receiver to report, quarantine, or reject emails that fail authentication checks. Policy options are: 1) p=none 2) p=quarantine or 3) p=reject. |
| adkim | Optional | It stands for DKIM alignment mode. Its value can be either Strict (s) or Relaxed (r).In relaxed mode, the verification will pass if the verified DKIM record belongs to a domain d=example.com, and the message is sent from [email protected]. In the strict mode, the check will be passed only if the email comes from an address on the example.com domain. Subdomains won’t pass validation. |
| aspf | Optional | The aspf DMARC tag stands for SPF alignment mode. Its value can be either Strict (s) or Relaxed (r). The default is Relaxed “r”. |
| sp (subdomain policy) | Optional | The DMARC sp tag specifies subdomain policy. The policy mode is configured for your main domain (p). |
| fo (failure reporting) | Optional | The default value of the DMARC fo tag is 0. It caters to the failure reporting options the domain owners can select from. The available options are: fo=0: a DMARC failure/forensic report is sent to you if your email fails both SPF and DKIM alignmentfo=1: a DMARC failure/forensic report is sent to you when your email fails either SPF or DKIM alignmentfo=d: a DKIM failure report is sent if the email’s DKIM signature fails validation, regardless of the alignmentfo=s: an SPF failure report is sent if the email fails SPF evaluation, irrespective of the alignment. |
| ruf (failure report RUI) | Optional but recommended | The DMARC ruf tag tells the address where DMARC forensic ruf report is to be delivered. At present, most reporting organizations don’t send forensic data. Specifying this tag implies that the owner requires recipient servers to send detailed reports on every message that fails DMARC validation. |
| rua (aggregate report RUI) | Optional but recommended | The DMARC rua tag specifies the email address or web server to which reporting organizations must deliver their DMARC aggregate rua data. It’s possible to specify mailto: links for sending reports by mail. |
| rf (report format) | Optional | This DMARC tag’s default value is ‘afrf’ and is used for noting the various formats for forensic reports. |
| pct (percentage) | Optional | Its default value is ‘100’. This tag shows the percentage of emails to which the policy mode applies. For example, “pct = 20” will filter 20% of emails. |
| ri (report interval) | Optional | The ri tag’s default value is ‘86400’. It specifies the time interval in seconds between two consecutive aggregate reports. The reports the domain owner by reporting organization. |
How To Set Up DMARC Record Using the Right Tags?
Since DMARC helps prevent spamming and phishing attacks attempted by exploiting your company’s name, it’s important to set up a DMARC record. Here’s what you have to follow:
- Contact your DNS administrator to create a TXT record in DNS for your domain.
- Ensure you have an A record, AAAA record, or Mail Exchange (MX) record in the DNS.
- Generate your DMARC record using the following DMARC tags in syntax: v=DMARC1; p=none; fo=1; rua=mailto: enter your URI (Uniform Resource Identifier); ruf=enter your URI. Or use our DMARC record generator below.
GENERATOR WIDGET
- Add the record to your DNS and start the journey towards DMARC compliance. If you’ve recently implemented DMARC protocol and are currently using p=none policy, we recommend that you monitor your domain activity for at least 30 days. After that, you can build the strategy that works best for DMARC policy advancement.
Summary
Threat actors use email domains of reputable organizations to send fraudulent messages for phishing and scamming. DMARC protects your domain using DMARC tags directing recipient’s server on how to treat legitimate and illegitimate emails from your domain.
DMARC tags ‘v’ and ‘p’ are mandatory, whereas ‘adkim’, ‘aspf’, ‘sp’, ‘fo’, ‘rf’, ‘pct’, and ‘ri’ are optional. DMARC ‘ruf’ tag and DMARC ‘rua’ tag are optional but recommended.
Using the correct tags and knowing their functionality will help you get the most out of your DMARC journey.
EasyDMARC Can Help!
Our DMARC Record Generator is a user friendly free tool that can be used without logging in. Set all the parameters and generate your DMARC record with proper syntax and tags in a few seconds.