In order to successfully add OpenDKIM to DNS on Linux, you need to understand some basic terms and tips.
3 must-know-terms to add Postfix DKIM to DNS
- The Basic terms in Email authentication, DNS records, and other related concepts.
- DMARC and the Email authentication process.
- Anatomy of a DMARC Resource record in the DNS.
If you are still hesitating to add OpenDKIM to DNS or not, here is interesting information and facts for you to make sure that email protection is your business trust, and for trust, it isn’t a good idea to save money.
Now you are convinced that it is important to add DKIM to DNS for your email protection. So, let’s go through wiht it.
Why do we evaluate the importance of email protection?
Easydmarc’s email protection services make your business safe and secure from cyber attacks and especially, from phishing and spoofing. Email protection isn’t the companies primary need only, but also it is your companies trust, authority, and future.
EasyDMARC solution
We understand your worries about cyber-risks. And because nowadays customer trust is the best future, thus we make your business trust our top priority. Email protection is what leads you to the bright future without any spam, phishing, and fraud.
We suggest awesome tools and advanced solutions to individuals and organizations of all spheres and sizes. Far beyond any shadow of a doubt, a data-driven solution ensures your business email top security, nonetheless enabling DMARC is a lot easier to understand, adopt and maintain. Thus whilst providing advanced email protection services we also ensure your business trust and reliability with our data-driven technologies. At Easydmarc, we provide a well-designed and user-friendly platform for getting full visibility of enlightened of your domain so as to do monitoring and get reports or alerts.
Did you know that threats cost for businesses is more than $5.3 billion and cannot be detected by solutions that detect only malware?
EasyDMARC also provides step-by-step instructions to help you set up, install and add OpenDKIM on DNS for multi-domains with Postfix on Linux.
Email authentication technologies
Email authentication isn’t new in the IT industry, moreover, it comes to the surface of the world a decade ago. From the 1980s with the Simple mail protocol aka SMTP creation, email authentication issues become more and more popular day by day and continuing its growth. Unfortunately, SMTP protocol doesn’t solve the problem of fraudulent and underhanded emails at all.
At this point in time, it suffices to say that the infallible statement ‘email infrastructure lies behind the scenes’ is further established with the premise that DNS records, email authentication, open and click tracking, domain alignment, and the contents embedded in email headers all play an indispensable role as they all together ensure the smooth run and easy access that a user gains into an inbox and its contents.
Email authentication solves phishing problems
It becomes more difficult to handle all email security issues when spammers and bots are laying behind the scene. Spammers and hackers make money one this, and phishing is easy as well as fast. Sometimes ‘spammers’ hide their identity to avoid being tracked often operating via forged email addresses thereby causing a great deal of difficulty in tracing a message back to its source. Hence, SPF, DKIM, DMARC ensure maximum security of email addresses which becomes vital. These include the terms
- Sender Policy Framework (SPF)
- DomainKeys Identified Mail (DKIM).
- DMARC- Domain-based Message Authentication, Reporting & Conformance.
After building a magic setup script coupled with an open source software bundle that enables a smooth encounter at transforming a server into a problem solver for emails with multiple domains, the following steps when strictly adhered aid in achieving the intended outcome we crave for.
You can download our magic script from here.
Here is how to go through the postfix DKIM setup and configure Postfix OpenDKIM for multiple domains with Postfix on Linux with the script below.
#!/bin/bash
if [[ "$1" != "INSTALL" ]]
then
echo "Note: please run from root user"
echo "This script will generate keys for domain and install openDkim postfix on this host"
echo "to process please use $0 INSTALL"
exit
fi
echo -n 'Enter Domain name : '
read domain_global
echo 'Specifies the selector, or name, of the key pair generated'
echo -n 'Enter group name/DNS (node|mail) : '
read group_name
echo Install opendkim and posfix
apt-get install -y opendkim opendkim-tools postfix mailutils
mkdir -p /etc/opendkim/${domain_global} &>/dev/null
echo ______________________________________________________________________________________
echo "Generate key for ${domain_global}:${group_name}"
opendkim-genkey -D /etc/opendkim/${domain_global} -d $domain_global -s $group_name
echo ______________________________________________________________________________________
echo 'Update keytable file'
echo "${group_name}._domainkey.${domain_global} ${domain_global}:${group_name}:/etc/opendkim/${domain_global}/${group_name}.private" >> /etc/opendkim/keytable
echo ______________________________________________________________________________________
echo 'Update signingtable file'
echo ${domain_global} ${group_name}._domainkey.${domain_global} >> /etc/opendkim/signingtable
echo ______________________________________________________________________________________
echo Configure OpenDKIM
echo 'SOCKET="local:/var/spool/postfix/var/run/opendkim/opendkim.sock"' > /etc/default/opendkim
mkdir -p /var/spool/postfix/var/run/opendkim &>/dev/null
cat > /etc/opendkim.conf <<EOF
Syslog yes
SyslogSuccess yes
LogWhy yes
UMask 002
SoftwareHeader yes
OversignHeaders From
Canonicalization relaxed/relaxed
KeyTable file:/etc/opendkim/keytable
SigningTable file:/etc/opendkim/signingtable
EOF
echo ______________________________________________________________________________________
echo 'Configure postfix '
postconf -e milter_default_action=accept
postconf -e milter_protocol=2
postconf -e smtpd_milters=unix:/var/run/opendkim/opendkim.sock
postconf -e non_smtpd_milters=unix:/var/run/opendkim/opendkim.sock
Download and rename txt file to an executable bash script.
Let’s go step by step with our installation script lines
You will need to run the script from the root user, the script will generate keys for a domain and install OpenDkim, Postfix on the host.
Enter a domain name, specify the selector after script will generate appropriate configurations.
After the successful installation, you will need to add very important DNS records for your domain.
We shall now examine each of the email authentication concepts one after the other.
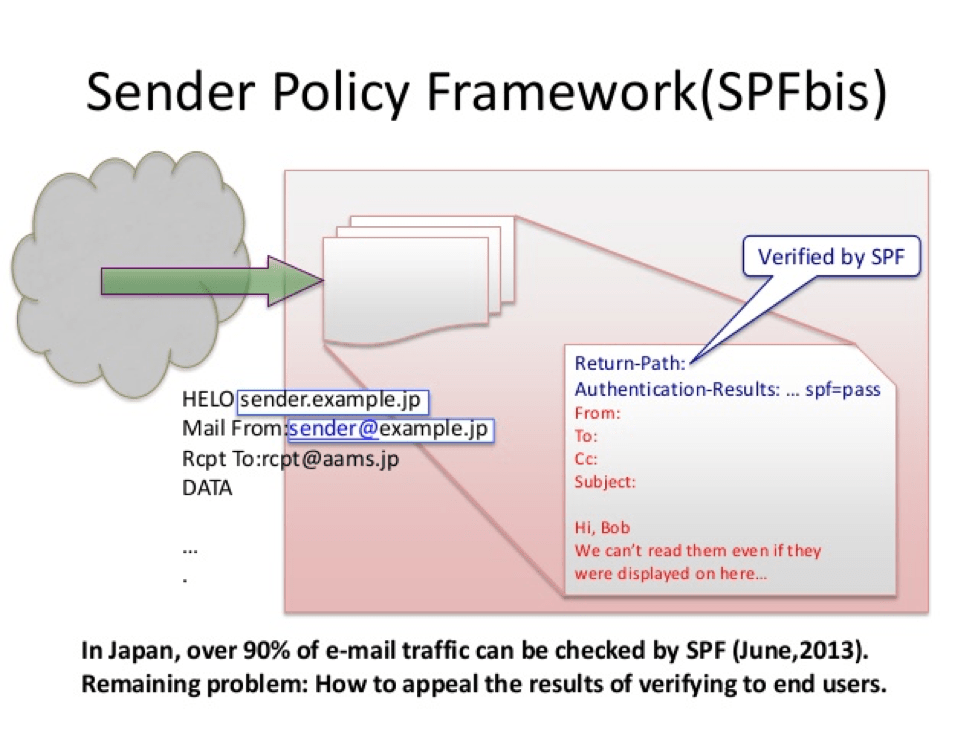
Sender Policy Framework (SPF)
This is a simple email-validation system that detects email spoofing by providing a mechanism that allows receiving mail exchangers to check that incoming mail from a domain comes from a host authorized by that domain’s administrators.
This can be achieved via configuring your SPF record with our SPF wizard.
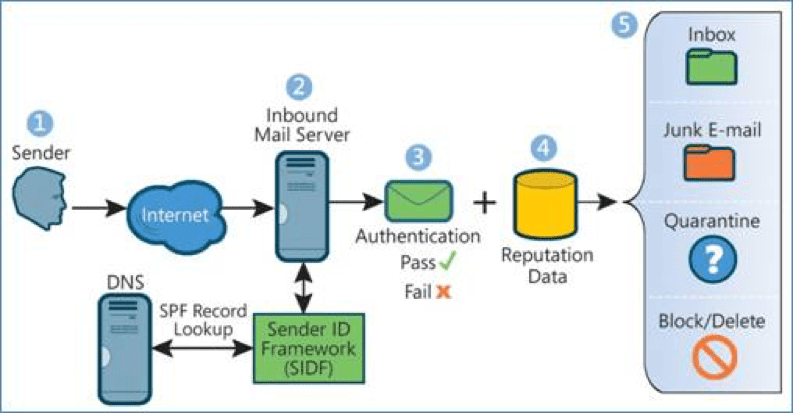
Under the SPF, messages that do not come directly from the return paths designated outbound servers we consider as forged. This semantic is compatible with existing practices, with two exceptions; web-generated email and verbatim forwarding. Those two cases should implement SRS for best results.
DKIM – DomainKeys Identified Mail (DKIM) is a protocol that permits a person, role, or organization that possesses ownership of a signing domain to claim some responsibility for a message via associating the domain with the message. This is an important authentication mechanism to help protect both email receivers and email senders from forged and phishing emails. Forged email is a serious threat to all parties in an email exchange. Our wizard for DKIM configuration and checks is here.
What is DMARC
Before going any further, let’s understand what is dmarc. A Domain-based Message Authentication Reporting and Conformance or DMARC is an email validation and reporting protocol which helps You protect Your email infrastructure from spoofing or phishing attacks. DMARC meets Your organization’s inbound email authentication needs. DMARC is based on two SPF and DKIM basic protocols which let a receiver and a sender to cooperate with each other in order to authenticate emails by sender SPF and a receivers DKIM.
What is EasyDMARC Trust?
With DMARC TRUST tools You will protect Your receivers email infrastructure from spoofed messages, in contrast with this, you will protect Your domain from illegitimate usage and spam content being sent on Your behalf.
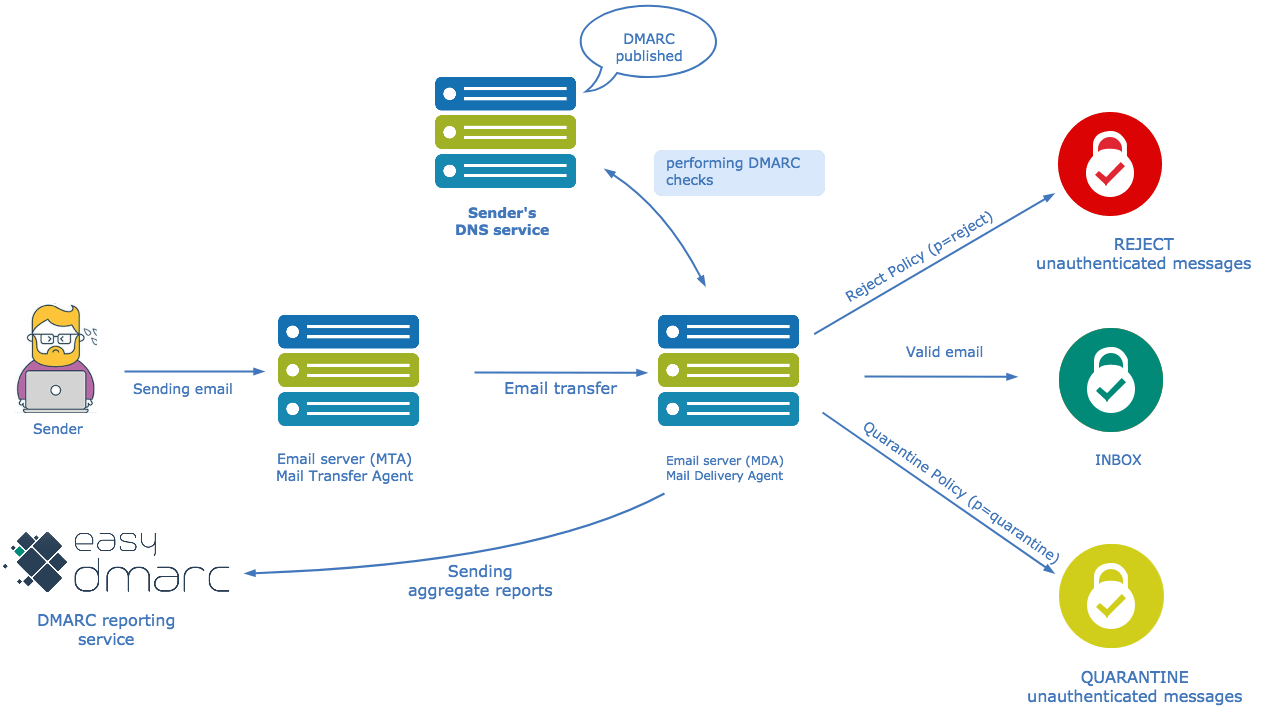
The goal of DMARC is to build on this system of senders and receivers collaborating to improve mail authentication practices of senders and enable receivers to reject unauthenticated messages. We have very useful tools and reporting mechanisms for the DMARC. Check them here. DMARC determines the real or not legitimate email sources. So if the message doesn’t pass DMARC authentification can handle the “non-aligned” messages fates. For example, in a scenario where a receiver deploys SPF and DKIM, plus its own spam filters, the flow is likely to result as shown:

Anatomy of a DMARC Resource Record in the DNS
DMARC policies are published in the DNS as text (TXT) resource records (RR). As stated earlier, they announce what an email receiver should do with the non-aligned mail it receives.
Consider an example DMARC TXT RR for the domain “sender.easydmarc.com” that reads:
“v=DMARC1;p=reject;pct=100;rua=mailto:[email protected]”
How Senders Deploy DMARC in 5-Easy Steps
DMARC is based on real-world experience by some of the world’s largest email senders and receivers deploying SPF and DKIM. The specification takes into account the fact that it is nearly impossible for an organization to flip a switch to production. There are a number of built-in methods for “throttling” the DMARC processing so that all parties can ease into full deployment over time.
- Deploy DKIM & SPF. You have to cover the basics, first.
- Ensure that your mailers are correctly aligning the appropriate identifiers.
- Publish a DMARC record with the “none” flag set for the policies, which requests data reports.
- Analyze the data and modify your mail streams as appropriate.
- Modify your DMARC policy flags from “none” to “quarantine” to “reject” as you gain experience.





